Exhibit 10.1
| FutureTech Systems Inc. | |
| Software Technology | |
| Service Contract | |
| Includes project quotation and technical solution |
Table of Contents
| Table of Contents | 1 |
| Software Technology Service Contract | 3 |
| Article 1: Contract Subject | 3 |
| Article 2: System Price and Payment | 4 |
| Article 3: Acceptance Standards | 5 |
| Article 4: Intellectual Property | 6 |
| Article 5: Confidentiality Obligations | 6 |
| Article 6: Liability for Breach of Contract | 7 |
| Article 7: Maintenance and Upgrades | 7 |
| Article 8: Applicable Law and Dispute Resolution | 8 |
| Article 9: Force Majeure | 8 |
| Article 10: Contract Modifications and Supplements | 9 |
| Article 11: Validity of Contract | 9 |
| Appendix 1: Project Quotation | 10 |
| Appendix 2: System Technical Solution | 13 |
| 1. Project Overview | 13 |
| 2. Project Overview and Requirements Analysis | 36 |
| 2.1 Functional Requirements Analysis | 36 |
| Basic Modules: | 36 |
| Customer Management Module: | 37 |
| Marketing Module: | 37 |
| Sales Module: | 38 |
| Project Management Module: | 39 |
| Product Module: | 39 |
| Reporting and Analysis Module: | 40 |
| Integration Module: | 40 |
| Knowledge Base Module: | 41 |
| Others: | 41 |
| 2.2 Non-Functional Requirements Analysis | 41 |
| 2.3 Other Requirements Analysis | 43 |
| III. Technical Implementation Plan | 45 |
| 3.1 System Architecture Design | 45 |
| 3.2 Key Technology Selection | 47 |
| 3.3 Functional Module Design | 48 |
| 3.4 Integration Plan | 56 |
| 3.5 Innovation Point Analysis | 57 |
| 4. Project Implementation Plan | 59 |
| 4.1 Project Organization Structure | 59 |
| 4.2 Project Process | 59 |
| Work Breakdown Structure: | 61 |
1
| Milestone Schedule: | 63 |
| Progress Schedule: | 63 |
| 5. Quality Assurance Measures | 64 |
| 5.1 Quality Control Process | 64 |
| 5.2 Testing Strategy | 65 |
| 5.3 Delivery Acceptance Criteria | 66 |
| 6. Risk Management Plan | 68 |
| 6.1 Technical Risks | 68 |
| 6.2 Time Risks | 68 |
| 6.3 Resource Risks | 69 |
| 6.4 Quality Risks | 69 |
| 6.5 Security Risks | 69 |
| 6.6 User Experience Risks | 69 |
| 6.7 Risk Management | 70 |
| 7. Project Deliverables | 70 |
| 7.1 Final Deliverables List | 70 |
| 7.2 Operations and Maintenance Support Plan | 71 |
| Monitoring and Alerts: | 71 |
| Maintenance and Updates: | 71 |
| Data Backup and Recovery: | 71 |
| Fault Handling: | 72 |
| Performance Optimization: | 72 |
| Customer Support: | 73 |
| Emergency Plans: | 73 |
| 8. Other Supporting Documents | 73 |
| 8.1 Company and Team Introduction |
2
Software Technology Service Contract
Party A (Client): Prestige Wealth Inc.
Party B (Supplier): FutureTech Systems Inc.
Considering that:
| 1. | Party A needs to procure an Intelligent Customer Relationship Management System (CRMAI) to improve customer service and investment management capabilities. |
| 2. | Party B is a professional software technology service company with the qualifications and capabilities to develop and deliver the aforementioned system. |
| 3. | To clarify the rights and obligations of both parties, the following contract terms are agreed upon through friendly negotiation: |
Article 1: Contract Subject
| 1.1 | Party B shall provide complete system customization, development, testing, delivery, and operation and maintenance services for Party A as per the content of “CRMAI System Quotation” in Appendix 1. |
| 1.2 | The delivered system shall comply with national and financial industry software standards, be functionally complete, and be of reliable and stable quality. |
| 1.3 | Party B promises to develop the system according to Party A’s requirements and complete it within the agreed time. |
| 1.4 | Party B shall submit a detailed project plan within 5 working days after the contract is signed, including project schedule, personnel configuration, and technical solutions. |
| 1.5 | During the project implementation process, Party B shall submit a weekly project progress report to Party A and hold project progress meetings to ensure the project proceeds as planned. |
3
Article 2: System Price and Payment
| 2.1 | The total contract price is USD 900,000, including software development, testing, delivery, implementation, and one year of free maintenance service. |
| 2.2 | If Party A fails to make timely payments, Party B has the right to suspend the project implementation until Party B receives payment from Party A. Delays caused by suspension do not constitute a breach of contract by Party B. |
| 2.3 | The compensation referred to in Section 2.1 above shall be paid by Party A to Party B, or to the company or individual designated by Party B in the form of (i) 1,500,000 newly issued restricted Class A ordinary shares of the Company (the “Shares”) at a price per share of US$0.60. (ii) warrants to purchase 750,000 Class A ordinary shares of the Company at an exercise price equal to US$0.72 (120% of the price per Class A ordinary share pursuant to clause (i) above) (the “Warrants”). The Warrants shall not be exercised until the date that is six months following the issuance date, shall have a term of 5 years and may be exercised on a cash or cashless basis in accordance with the terms of the Warrants. The Warrant is in substantially the form attached hereto as Exhibit A. |
In connection with the issuance of the Shares, Party B hereby represents and warrants to Party A, and covenants for the benefit of Party A, as follows:
| (a) | It is an “accredited investor” as defined under Rule 501 of Regulation D promulgated under the Securities Act of 1933, as amended (the “Securities Act”); |
| (b) | It is acquiring the Shares for its own account and not with a view to any distribution of the Shares in violation of the Securities Act; |
| (c) | It has significant prior investment experience, including investment in non-listed and non-registered securities, and recognizes the highly speculative nature of this investment. It has been furnished with all documents and other information regarding Party A that it had requested or desired to know and all other documents which could be reasonably provided have been made available for its inspection and review; |
| (d) | It acknowledges that the Shares have not been passed upon or reviewed by the U.S. Securities and Exchange Commission (the “Commission”). It agrees that it will not sell, transfer or otherwise dispose of any of the Shares unless they are registered under the Securities Act, or unless an exemption from such registration is available. It understands that the Shares have not been registered under the Securities Act by reason of a claimed exemption under the provisions of the Securities Act; |
4
| (e) | It acknowledges that the Shares were not offered to Party B by means of any form of general or public solicitation or general advertising, or publicly disseminated advertisements or sales literature, including (i) any advertisement, article, notice or other communication published in any newspaper, magazine, or similar media, or broadcast over television or radio, or (ii) any seminar or meeting to which Party B was invited by any of the foregoing means of communications; |
| (f) | Party B understands that the Shares must be held indefinitely unless such Shares are registered under the Securities Act or an exemption from registration is available. Party B acknowledges that it is familiar with Rule 144, of the rules and regulations of the Commission, as amended, promulgated pursuant to the Securities Act (“Rule 144”), and that such person has been advised that Rule 144 permits resales only under certain circumstances. Party B understands that to the extent that Rule 144 is not available, it will be unable to sell any Shares without either registration under the Securities Act or the existence of another exemption from such registration requirement; and |
| (g) | Party B understands that the Shares are being offered and sold in reliance on a transactional exemption from the registration requirements of U.S. federal and state securities laws and Party A is relying upon the truth and accuracy of the representations, warranties, agreements, acknowledgments and understandings of Party B set forth herein in order to determine the applicability of such exemptions and the suitability of Party B to acquire the Shares. |
Article 3: Acceptance Standards
| 3.1 | Party B shall develop various functional modules and perform integration testing to ensure the system quality meets the requirements, as specified in the “CRMAI System Quotation.” |
| 3.2 | Party A shall conduct comprehensive inspections and tests on the system’s functional completeness, usability, performance, and security. Final acceptance shall only be deemed complete after all acceptance test cases pass. |
| 3.3 | If serious defects are found during acceptance, Party B must rectify them according to Party A’s requirements until they meet the acceptance standards. |
| 3.4 | Party B shall complete all rectification work within 10 working days after receiving Party A’s acceptance feedback. |
5
| 3.5 | Detailed acceptance standards are provided in Appendix 2 “System Technical Solution,” including specific functional requirements, performance indicators, and security standards. |
| 3.6 | During the acceptance period, Party A shall provide the necessary testing environment and data to assist Party B in completing all acceptance tests. |
Article 4: Intellectual Property
| 4.1 | The intellectual property rights of the system software developed under this contract belong to Party A. Party B shall provide the source code and related technical documents. |
| 4.2 | Party A has the permanent right to use the system and shall not transfer or provide the right to use it to any third party. |
| 4.3 | Party B shall ensure that the software and its technical solutions provided do not infringe on any third party’s intellectual property rights. If infringement occurs, Party B shall bear all legal responsibilities. |
Article 5: Confidentiality Obligations
| 5.1 | Both parties have confidentiality obligations regarding technical, commercial secrets, and other confidential information learned during contract performance. |
| 5.2 | Without the other party’s written consent, neither party shall disclose the aforementioned confidential information to any third party, nor use it for purposes other than contract performance. |
| 5.3 | If a breach of confidentiality occurs, the breaching party shall bear the direct economic losses caused to the non-breaching party and pay a penalty for breach of contract. |
| 5.4 | Confidentiality obligations shall remain effective after the contract is terminated, with a duration of two years after termination. |
| 5.5 | Party B shall take reasonable technical and management measures to ensure the security and confidentiality of Party A’s data. During system development, testing, implementation, and maintenance, Party B shall strictly control data access rights and record and review related operations. |
| 5.6 | During project implementation, Party B shall not use Party A’s data for any purposes other than those agreed in the contract, nor provide the data to third parties. |
6
Article 6: Liability for Breach of Contract
| 6.1 | If Party B fails to deliver the system on time or the delivered system fails to meet acceptance standards, Party B shall pay Party A a penalty of 0.2% of the contract amount for each 7 days of delay. |
| 6.2 | If Party A fails to make timely payments, Party A shall pay Party B a penalty of 0.2% of the corresponding installment for each 7 days of delay. |
| 6.3 | If the accumulated penalty for any party exceeds 10% of the total contract amount, the non-breaching party has the right to terminate the contract and claim other losses caused by the breach. |
| 6.4 | If Party B causes system or data damage due to negligence during contract performance, Party B shall bear the corresponding restoration and compensation responsibilities. |
| 6.5 | If Party B fails to complete the project progress according to the contract schedule, Party A has the right to require Party B to increase the project team members or take other measures to expedite the project progress and ensure the project is completed on time. |
| 6.6 | If Party A fails to provide the necessary resources, cooperation, or environment as agreed during project implementation, resulting in project progress delays, Party B shall not bear the corresponding breach of contract responsibility. |
Article 7: Maintenance and Upgrades
| 7.1 | After the system passes acceptance, Party B shall provide one year of free maintenance service for Party A. |
| 7.2 | After the one-year period, if Party A needs continuous maintenance services, Party B shall charge an annual fee, not exceeding 10% of the system price for that year. |
| 7.3 | Party B shall continue to provide optimization and upgrade services for the system, with upgrade content and fees negotiated separately. |
| 7.4 | During the maintenance period, Party B shall respond within 4 hours after receiving Party A’s issue report and propose a solution within 24 hours. |
| 7.5 | Party B shall provide regular inspection services for the system, identify potential issues and handle them promptly to ensure stable system operation. Inspection services include system performance optimization, security vulnerability repairs, log analysis, etc. |
7
| 7.6 | Party B shall provide system usage training for Party A, ensuring that Party A’s related personnel master the basic operations and maintenance methods of the system. Training content includes system function introduction, operation process demonstration, and common problem handling. |
Article 8: Applicable Law and Dispute Resolution
| 8.1 | The conclusion, validity, interpretation, execution, and dispute resolution of this contract are governed by Hong Kong laws and relevant international laws and regulations. |
| 8.2 | In case of disputes during contract performance, both parties shall first negotiate amicably. For disputes, both parties agree to submit to International Arbitration in accordance with its current arbitration rules. The arbitration award is final and binding on both parties. |
| 8.3 | During the dispute resolution process, both parties shall continue to perform the terms of the contract that are not in dispute to ensure the normal progress of the project. |
| 8.4 | During the dispute resolution process, both parties shall jointly protect each other’s trade secrets and technical information and shall not disclose or leak relevant information due to the dispute. |
Article 9: Force Majeure
| 9.1 | If either party is unable to perform the contract due to force majeure events (such as natural disasters, wars, strikes, government actions, etc.), it shall promptly notify the other party in writing after the force majeure event occurs and provide details of the force majeure event and valid proof of contract non-performance or delayed performance within a reasonable time. |
| 9.2 | If the contract performance is difficult or delayed due to a force majeure event, both parties shall decide through amicable negotiation whether to terminate the contract or partially exempt the performance obligations. |
| 9.3 | After the force majeure event ends, the affected party shall resume contract performance as soon as possible and notify the other party of the specific situation and the resumption time. |
8
| 9.4 | During the force majeure event, both parties shall minimize losses and jointly discuss reasonable remedial measures. |
Article 10: Contract Modifications and Supplements
| 10.1 | Any modification or supplement to this contract shall be made in writing and confirmed by both parties’ signatures or seals. |
| 10.2 | Contract modification and supplement documents have the same legal effect as this contract. |
| 10.3 | If any contract terms need to be modified due to changes in laws and regulations, both parties shall modify them according to the latest legal requirements to ensure the legality and validity of the contract. |
| 10.4 | If any clause of the contract is deemed invalid or unenforceable, it does not affect the validity of the other clauses of the contract. Both parties shall negotiate to modify the clause to align with the original intention and purpose of the contract. |
Article 11: Validity of Contract
| 11.1 | This contract shall come into effect upon being stamped by both parties or signed by their legal representatives or authorized agents. |
| 11.2 | This contract, together with the “CRMAI System Quotation” and “System Technical Solution” appendices, is an inseparable whole and has the same legal effect. |
| 11.3 | This contract is made in three copies, with Party A and Party B each holding one copy, and one copy retained by the Ministry of Commerce for archiving. |
| 11.4 | During contract performance, if either party changes its name, address, contact information, etc., it shall promptly notify the other party in writing to ensure effective contract performance and smooth communication between the parties. |
| Party A (Seal): | ||
| Party B (Seal): | ||
| Party A’s Legal Representative (Signature): | /s/ Hongtao Shi | |
| Party B’s Legal Representative (Signature): | /s/ Shan He | |
| Signing Date: July 1, 2024 |
9
Appendix 1: Project Quotation
Intelligent Customer Relationship Management System (CRMAI)
Quotation
Client:
Date: May 1, 2024
| Category | Functional Module | Development Person-Days |
Daily Rate ($) |
Estimated
Price ($) |
| Portal Entry | Intelligent Financial Portal |
15 | 400 | 6,000 |
| CRM | Intelligent Customer Relationship Management Platform |
180 | 550 | 99,000 |
| Investment Management | Global Investment Portfolio Management System |
200 | 600 | 120,000 |
| Risk Control and Compliance | Intelligent Risk Control and Compliance Management System |
210 | 600 | 126,000 |
System Integration |
Fintech Integration Platform |
110 | 500 | 55,000 |
| Collaborative Office | Intelligent Calendar and Appointment Scheduling Tool |
40 | 400 | 16,000 |
| Collaborative Office | Intelligent Document Management and Customer Collaboration Platform |
35 | 400 | 14,000 |
10
| Marketing Management | Marketing Automation and Email Engine |
90 | 500 | 45,000 |
| Marketing Management | Intelligent Marketing and Lead Development System |
130 | 500 | 65,000 |
| Collaborative Office | Intelligent Call Management and Recording System |
25 | 400 | 10,000 |
| Collaborative Office | Video Conferencing and Online Collaboration Platform |
35 | 400 | 14,000 |
| Collaborative Office | Intelligent Task Assignment and Tracking System |
25 | 400 | 10,000 |
| Customer Management | Customer Information and Notes Management Tool |
15 | 400 | 6,000 |
| Financial Management | Intelligent Billing and Payment Collection System |
100 | 500 | 50,000 |
| Contract Management | Electronic Contract and Signing Management Platform |
90 | 500 | 45,000 |
| Service Support | Customer Service and Case Knowledge Base |
80 | 450 | 36,000 |
| Customer Analysis | Target Customer Identification and Analysis System |
110 | 500 | 55,000 |
| Customer Analysis | Potential Customer Lead Management System |
70 | 450 | 31,500 |
| Investment Management | Investment Portfolio Project Management Platform |
180 | 550 | 99,000 |
11
| Investment Management | Investment Plan Templates and Configuration Library |
80 | 450 | 36,000 |
| Marketing Management | Marketing Event and Roadshow Management System |
110 | 500 | 55,000 |
| Resource Management | Facility and Resource Allocation System |
25 | 400 | 10,000 |
| Product Management | Financial Product and Service Management Platform |
130 | 500 | 65,000 |
| Product Management | Financial Product Classification and Tag Management |
70 | 450 | 31,500 |
| Investment Management | Investment Report and Recommendation Template Library |
80 | 450 | 36,000 |
Report Analysis |
Wealth Analysis and Reporting Center |
130 | 500 | 65,000 |
Knowledge Management |
Wealth Management Knowledge Base |
110 | 500 | 55,000 |
| Knowledge Management | Wealth Knowledge Intelligent Classification and Recommendation |
50 | 450 | 22,500 |
| Marketing Management | Marketing Email Design and Sending System |
70 | 450 | 31,500 |
| Customer Service | Customer Survey and Feedback Collection Platform |
100 | 500 | 50,000 |
Mobile Terminal |
IOS/Android Mobile Financial Client |
800 | 300 | 240,000 |
Total Development Person-Days: 3495 Person-Days
Total Estimated Price: $1,200,000
Discount Price: $900,000
Note:
| ● | The total quotation is $900,000 to ensure high-quality project delivery. |
| ● | The price includes software development, testing, deployment, and one year of maintenance services. |
12
Appendix 2: System Technical Solution
Intelligent Customer Relationship Management System (CRMAI)
Project Plan
1. Project Overview
1.1 Project Background
Shengde Wealth is a leading wealth management listed company, providing comprehensive wealth management solutions for high-net-worth clients. As the business continues to expand, the customer base is growing larger, and the company faces higher digital transformation needs, hoping to achieve business process optimization, customer experience enhancement, operational efficiency improvement, and compliance management goals through the construction of an advanced intelligent customer relationship management system (CRMAI).
The company’s existing traditional customer relationship management cannot fully meet the business development needs, with issues such as information silos, inefficient processes, and weak marketing capabilities. Through this information construction, we hope to build a one-stop intelligent platform that integrates customer management, marketing, investment portfolio, compliance, and business intelligence, helping the company achieve digital transformation and enhance core competitiveness.
To break through development bottlenecks and achieve leapfrog growth, the company plans to launch a global comprehensive wealth management solution as the core tool for implementing the “global integration” strategy. This solution will integrate the company’s core technological advantages to build an integrated platform covering customer development, advisory transactions, risk management, data analysis, and other aspects, achieving closed-loop management of business processes and providing customers with a “one-stop” high-quality wealth management experience.
The company will adhere to the concept of “global vision, local service,” quickly expanding its coverage in major global markets such as Greater China, Southeast Asia, Japan, Korea, and North America, through a combined online and offline customer acquisition model, planning to grow the number of effective global customers to 5,000-8,000 within 1-2 years.
13
This solution features an innovative open system architecture that can seamlessly integrate with third-party financial institutions, investment analysis tools, and has the expansion capability to quickly interface with artificial intelligence technologies such as ChatGPT, providing personalized intelligent advisory and management recommendations to customers.
This project is a key part of the company’s “technology empowerment, global intelligence” development strategy.
1.2 Project Goals
Business Goals:
| ● | Optimize Business Processes: Achieve automation and optimization of business processes through the advanced CRMAI system, reducing manual operations and improving work efficiency. |
| ● | Enhance Customer Experience: Provide more personalized and intelligent services to enhance customer satisfaction and loyalty. |
| ● | Improve Operational Efficiency: Simplify operational processes by integrating customer management, marketing, investment portfolio management, compliance management, and business intelligence functions, and improve overall operational efficiency. |
| ● | Strengthen Compliance Management: Ensure business operations comply with relevant regulations and policies through systematic compliance management functions, reducing compliance risks. |
| ● | Achieve Global Development Strategy: Build a comprehensive wealth management solution covering major global markets, promoting the company’s rapid expansion in markets such as Greater China, Southeast Asia, Japan, Korea, and North America. |
| ● | Breakthrough Development Bottlenecks, Achieve Leapfrog Growth: Break through existing business bottlenecks through innovative technologies and open system architecture, promoting the company’s business to achieve leapfrog growth. |
| ● | Achieve Closed-loop Management of Business Processes: Integrate customer development, advisory transactions, risk management, data analysis, and other links to form an integrated platform and achieve closed-loop management of business processes. |
14
| ● | Enhance Core Competitiveness: Enhance the company’s core competitiveness through digital transformation and technological innovation, maintaining market leadership. |
| ● | Provide a One-stop High-quality Wealth Management Experience: Provide customers with one-stop services covering all wealth management needs and improve the overall customer experience. |
| ● | Achieve Technology Empowerment, Global Intelligence: Achieve technology empowerment through advanced CRMAI systems and global layout, promoting the intelligent and global development of the company’s business. |
System Goals:
| ● | Build an Integrated Intelligent Customer Relationship Management Platform: Integrate CRM, marketing, investment, compliance, and other core business systems. |
| ● | Break Information Barriers between Front-end Marketing and Mid-end Operations: Achieve data sharing and seamless collaboration between the front-end marketing system and the mid-end operations system. |
| ● | Empower New Business Models with Emerging Technologies: Use artificial intelligence and other emerging technologies to empower intelligent marketing, intelligent advisory, and intelligent risk control. |
| ● | Establish Efficient Business Analysis and Decision Support Systems: Enhance data-driven operations and business intelligence capabilities. |
| ● | Open System Architecture Design: Adopt innovative open system architecture to ensure good scalability and flexibility, seamlessly integrate with third-party financial institutions, investment analysis tools, and support continuous iteration and optimization. |
| ● | High Security and Compliance Assurance: Ensure high security and compliance in system design and development to protect customer data and business security. |
| ● | Full-channel Customer Reach and Management: Cover the entire process of customer development, service, and marketing through a combination of online and offline methods, improve customer reach efficiency and management levels, and ensure consistent and high-quality customer experience. |
| ● | Enhance Customer Data Management and Mining Capabilities: Establish a sound customer data management mechanism to improve the integrity, accuracy, and timeliness of customer data, gain deep insights into customer needs through data mining and analysis, and provide personalized services and products. |
15
| ● | Global Deployment and Support: Support global deployment of the system, meet the business needs of different regions and markets, and ensure stable operation and efficient support of the system in markets such as Greater China, Southeast Asia, Japan, Korea, and North America. |
| ● | Continuous Technological Innovation and Optimization: Maintain continuous technological innovation and optimization, continuously introduce advanced technologies and concepts, ensure the system always stays at the industry-leading level, and promote the continuous development and competitiveness of the company’s business. |
Organizational Goals:
| ● | Consolidate the Company’s Digital Infrastructure: Promote the digital transformation process of the enterprise. |
| ● | Improve IT System and Business Coordination Agility: Respond to business changes and innovation needs. |
| ● | Cultivate a Team of Compound Talents: Enhance technological innovation capabilities and digital operation levels. |
1.3 Project Scope Business Scope:
This project will cover the core business processes of the company’s wealth management, including:
| ● | Customer management (customer information, customer segmentation, customer relationships, etc.) |
| ● | Marketing management (marketing activities, potential customer management, lead conversion, etc.) |
| ● | Portfolio management (investment advice, transaction execution, risk monitoring, etc.) |
| ● | Compliance management (anti-money laundering, risk assessment, information disclosure, etc.) |
| ● | Business intelligence (reports, analysis, decision support, etc.) |
System Scope:
This project will build an intelligent CRM platform integrating customer management, marketing, portfolio, compliance, and business intelligence. The main system modules include:
| ● | Core CRM module (customers, opportunities, activities, contacts, etc.) |
16
| ● | Marketing automation module (marketing resources, activity execution, lead management, etc.) |
| ● | Portfolio management module (portfolio, transactions, risk analysis, etc.) |
| ● | Compliance control module (anti-money laundering, risk assessment, information disclosure, etc.) |
| ● | Business intelligence module (multi-dimensional analysis, mobile reports, visualization, etc.) |
| ● | Support module (workflow, knowledge base, schedule, email, etc.) |
Technical Scope:
| ● | System Architecture Design and Development |
| o | System Architecture Design |
| § | Overall Architecture Design: Determine the overall architecture model of the system, such as microservice-based distributed architecture, SOA-based service architecture, etc., and plan the hierarchical structure and component topology of the architecture. |
| § | Technical Architecture Design: Select and design the core technical architecture required by the system, such as application architecture (frontend architecture, middleware architecture), data architecture (relational database, NoSQL, data lake, etc.), infrastructure (operating system, virtualization, containers, etc.). |
| § | Security Architecture Design: Plan the overall architecture of system security protection, such as authentication, access control, data encryption, auditing, etc. |
| § | Integration Architecture Design: Design the integration architecture for interfacing with legacy systems and external systems, such as integration frameworks, message queues, ESB, etc. |
| o | System Development |
| § | System Framework Construction: Based on the architecture design, build the basic framework of the system, integrating related middleware, development tools, etc. |
| § | Development of Common Base Components: Develop the common technical components required by the system, such as workflow engine, rules engine, reporting engine, message middleware, etc. |
| § | Core Business Function Development: According to business requirements and system design, realize the development of various core functional modules, including customer management, marketing management, investment management, compliance management, etc. |
17
| § | Non-Functional Requirement Development: Implement the system’s non-functional requirements, such as performance, availability, scalability, security, etc. |
| § | Frontend UI Development: Develop intelligent interactive frontend interfaces to provide a good user experience for different terminals (PC, mobile, iOS, and Android). |
| § | Support for multiple languages: Chinese, English, Japanese, Arabic, French, Italian, Turkish, Norwegian, German, Hindi, etc. |
| § | System Integration and Data Migration: Achieve seamless integration with existing legacy systems/third-party systems and complete the migration of historical data. |
| § | Automated Testing: Design and develop automated testing frameworks and cases, including functional testing, performance testing, security testing, etc. |
| § | Deployment and Release: Complete the system deployment and go-live, formulate release strategies and rollback plans, etc. |
| ● | Data Integration (Legacy System Data Migration) |
| o | Data Source System Assessment |
| § | Fully identify and evaluate all existing legacy systems, data warehouses, reporting systems, and other data source systems to ensure coverage of all relevant data objects. |
| § | Perform data model analysis, data quality evaluation, and interface capability assessment for each data source and document the status. |
| § | Meanwhile, sort out business requirements to determine the key data objects that need to be integrated and migrated, and prioritize them. |
| o | Data Integration Architecture Planning |
| § | Design a flexible and scalable technical architecture based on the complexity of the data sources, integration scale, performance requirements, etc. |
| § | Recommend deploying reliable data integration tools (such as Informatica, Ab Initio, Talend, etc.) to meet efficient and stable data exchange requirements. |
18
| § | Develop a comprehensive data integration process, job scheduling, monitoring and alerting, fault-tolerant handling mechanisms. |
| § | Design a unified and efficient target data storage model based on the company’s data standards, and formulate data mapping and conversion rules. |
| o | Data Extraction Development |
| § | Develop high-performance data extraction interface programs for each source system based on the architecture and tools. |
| § | Support both online real-time and offline batch extraction modes and have the capability to capture incremental data. |
| § | Ensure the extraction program is stable and efficient with minimal impact on the source system performance. |
| o | Data Transformation and Loading |
| § | Perform all necessary data transformations, such as format standardization, code conversion, data quality checks, and cleaning. |
| § | Strictly apply data mapping and conversion rules to ensure accurate consistency between source data and target data. |
| § | Execute efficient batch loading and real-time incremental loading to the target system according to different business needs. |
| § | Implement concurrent loading control, validation processing, performance tuning, and other optimization measures. |
| o | Data Validation and Reconciliation |
| § | Establish end-to-end data integrity, consistency, and compliance validation mechanisms. |
| § | Periodically perform automated data validation and generate easy-to-understand exception reports. |
| § | Provide functions and processes that support manual reconciliation and feedback handling. |
| o | Operational Assurance |
| § | Build a dynamic monitoring platform for integration jobs, supporting proactive alerts and fault notifications. |
| § | Establish job scheduling management mechanisms, supporting automated rescheduling of failed jobs. |
| § | Implement unified logging and auditing functions, providing secure and traceable operation history. |
| § | Introduce version control mechanisms to ensure safe and controllable code changes. |
19
| o | Security and Compliance |
| § | Fully assess and comply with industry internal and external data security and privacy protection regulations. |
| § | Adopt comprehensive protection measures for sensitive data, such as encrypted storage and encrypted transmission. |
| § | Formulate and implement detailed data access control strategies to ensure compliant data usage. |
| ● | System Integration (External System Docking) |
| § | Integration with AIGC-related Systems |
| ● | Core Function Development and Customization |
| o | Customer Management Module |
| § | Customer Basic Information Management: Able to comprehensively record detailed information of individual customers and institutional customers, including contact information, occupation, income level, investment preferences, etc., to help account managers fully understand customer situations. |
| § | Customer Segmentation and Tag Management: Segment customers into different levels and categories based on their value, potential, risk, etc., and apply personalized tags to help formulate differentiated service strategies. |
| § | Customer Relationship Network Analysis and Profiling: Analyze customers’ social networks, transaction records, browsing footprints, etc., to create a comprehensive customer profile, deeply exploring customers’ investment needs and potential. |
| § | Customer Lifecycle and Value Assessment: Conduct detailed segmentation and value assessment of customers’ lifecycles and provide personalized contact strategies at different stages to maximize customer retention and development. |
| § | Customer Service and Interaction Tracking: Fully record all interactions between customers and the company, including meetings, phone calls, emails, etc., to help account managers efficiently manage customer relationships. |
| § | Potential Customer Demand Identification and Mining: Based on big data analysis and AI algorithms, intelligently identify customers’ potential investment needs and provide account managers with personalized demand development suggestions. |
20
| o | Marketing Management Module |
| § | Marketing Activity Planning and Execution: Support marketing teams in formulating annual marketing activity plans and controlling and tracking the execution process of marketing activities. |
| § | Marketing Resource and Channel Management: Centrally manage the company’s marketing resources and channel information, optimizing the allocation and use of marketing resources. |
| § | Potential Customer Lead Management: Collect and manage all potential customer lead information and assign it to appropriate account managers for development and follow-up. |
| § | Intelligent Lead Allocation and Priority Assessment: Based on factors such as the value and matching degree of leads, intelligently allocate leads to suitable account managers and dynamically assess the priority of leads. |
| § | Marketing Automation Process Design: Design various marketing automation process templates, such as email marketing, online marketing, etc., to improve marketing efficiency. |
| § | Marketing Performance Analysis: Conduct comprehensive analysis of marketing activities’ effectiveness and ROI to provide a basis for optimizing subsequent marketing strategies. |
| o | Portfolio Management Module |
| § | Portfolio Management and Optimization: Construct a reasonable investment portfolio for customers, meeting their return targets and risk preferences, and monitor and optimize the portfolio in real time. |
| § | Product and Asset Allocation Recommendations: Recommend suitable products and asset allocation plans for customers based on their investment goals and risk tolerance. |
| § | Transaction Execution and Verification: Provide efficient and convenient transaction execution channels for customers and conduct strict compliance checks on the transaction process. |
| § | Position Monitoring and Stop-Loss/Take-Profit: Monitor portfolio position changes in real time and take action promptly when the preset stop-loss/take-profit line is reached. |
| § | Risk Assessment and Stress Testing: Conduct comprehensive risk assessments of the portfolio and perform rigorous stress tests. |
| § | Performance Analysis and Attribution: Analyze the sources of investment performance to provide a basis for optimizing investment strategies. |
21
| ● | Compliance Management Module |
| o | Anti-Money Laundering Monitoring and Review Processes: Follow regulatory requirements to review customers’ identities, fund sources, and transaction activities to prevent illegal activities such as money laundering. |
| o | Customer Risk Level Assessment and Management: Assess and manage customers’ risk levels based on factors such as their background and investment behavior. |
| o | Information Disclosure and Regulatory Reporting Compliance: Ensure that the company’s information disclosure and regulatory reporting comply with legal and regulatory requirements. |
| o | Compliance Audits and Inspections: Regularly conduct compliance audits and inspections of the company’s business to timely identify and correct compliance risks. |
| o | Compliance Knowledge Base and Training: Establish a comprehensive compliance knowledge base and conduct compliance training to enhance employees’ compliance awareness and capabilities. |
| ● | AI Empowerment Module |
| o | Intelligent Q&A and Service Robots: Develop intelligent Q&A and service robots based on natural language processing technology to provide 24/7 consulting services, significantly improving customer service efficiency. |
| o | Intelligent Marketing Reach and Activity Recommendations: Based on customer profiles and behavioral data, intelligently recommend personalized marketing activities and contact methods to improve marketing conversion rates. |
| o | Natural Language Processing and Sentiment Analysis: Process and analyze customers’ text and voice data, such as emails and recordings, to deeply understand customer needs. |
| o | Investment Decision Assistance and Risk Warnings: Provide auxiliary suggestions for investment decisions based on machine learning algorithms and promptly warn of investment risks. |
| o | Intelligent Process Automation: Apply machine learning and natural language processing technologies to business processes to achieve intelligent management and automated execution of processes. |
22
| ● | Business Intelligence and Reporting Module |
| o | Multi-Dimensional Data Analysis and Visualization: Support multi-dimensional analysis of business data from multiple perspectives and intuitively present analysis results in the form of graphs and reports. |
| o | Personalized Report Design and Presentation: Users can design and generate various required reports according to their needs and save them as personalized templates for reuse. |
| o | Mobile BI and Data Dashboard: Users can query data and view reports through mobile terminals, and the company can also deploy data dashboards to display key business indicators in real time. |
| o | AI-Assisted Report Automatic Generation: Based on machine learning technology, the system can automatically generate commonly used reports, saving users’ design and production time. |
| o | Predictive Analysis and Decision Optimization: Provide forward-looking analysis for business decisions through data mining and predictive modeling and give optimization suggestions. |
| ● | Business Process and Support Module |
| o | Business Process Design and Automation: Flexibly define and optimize various process models according to the company’s actual business scenarios and automatically drive the approval and execution of processes. |
| o | Customer Service Process Management: Standardize the management of the entire process of customer service to ensure service quality, such as consultations and complaints. |
| o | Document Management and Knowledge Base Submodule: Centrally store and manage various documents of the company, including product manuals, operation guides, legal contracts, etc., realizing version control and permission management of documents. |
| o | Schedule and Task Collaboration Submodule: Employees can use this module for personal schedule arrangements and task assignments and also share and collaborate in real-time with other team members. |
| ● | System Integration and Data Exchange Module |
| o | Integration with Existing Company Systems: Achieve seamless integration with the company’s existing core business systems (such as transaction systems, account systems, etc.) to realize data sharing and business collaboration. |
| o | Interface with External Banking Systems: Interface with external banking systems through financial industry standard interfaces to facilitate customers’ fund transfer operations. |
23
| o | Fund Company Product Data Interface: Obtain real-time product data from fund companies to provide customers with the latest investment target information. |
| o | Regulatory System Reporting Interface: Built-in regulatory reporting interface to ensure timely and accurate submission of the company’s business data to regulatory authorities. |
| ● | Customized Requirement Development Module |
| o | Special Function Requirement Custom Development: Custom develop and integrate special functional modules according to customers’ personalized needs. |
| o | Introduction of Industry Best Practices: Introduce mature best practices in the financial industry into the system to improve the standardization and normative level of business processes. |
| o | Embedding of Company-Specific Business Processes: Embed the unique business processes of the customer company into the system to fit the actual business scenarios to the maximum extent. |
| o | Personalized UI Design: Professional designers can tailor personalized system UI according to the customer’s corporate culture and aesthetic preferences. |
Testing (Functional Testing, Performance Testing, Security Testing, etc.)
| ● | Functional Testing |
| o | Unit Testing: Developers verify the smallest testable units at the code level to ensure the correctness of individual functional points. |
| o | Integration Testing: Conduct integration testing for the interrelated modules in the system to check the integration quality and interoperability of the modules. |
| o | System Testing: Perform end-to-end system testing on the fully deployed application, simulating real user scenarios and business processes. |
| o | User Scenario Testing: Design various typical and boundary user scenario use cases, focusing on verifying the system’s robustness in complex scenarios. |
| o | Compatibility Testing: Test in many environments such as different browsers, operating systems, databases, etc., to ensure good compatibility of the system. |
| o | Installation Package Testing: Perform comprehensive testing on the final product installation package by repeatedly installing and uninstalling it on multiple devices. |
24
| ● | Non-Functional Testing |
| o | Performance Testing |
| § | Load Testing: Simulate different access pressures and data volumes to evaluate the load capacity and response time of the application. |
| § | Stress Testing: Continuously increase pressure until reaching the limit to understand the system’s stress bottleneck and optimize it. |
| § | Stability Testing: Apply a certain pressure continuously for a long time to check if the system runs stably without memory leaks, etc. |
| o | Security Testing |
| § | Penetration Testing: Simulate hacker methods to attempt attacking the system to detect potential threats and vulnerabilities. |
| § | Vulnerability Scanning: Use automated tools to scan the source code and runtime security vulnerabilities and manually verify them. |
| § | Compliance Audit: Evaluate whether the system complies with regulations and industry standards in terms of data protection and privacy. |
| o | Usability Testing |
| § | Ease of Use Testing: Evaluate the system’s operability, whether it fits users’ cognition and usage habits. |
| § | Accessibility Testing: Check if the system is accessible and operable for people with disabilities and meets accessibility requirements. |
| o | Other Testing |
| § | Concurrency Testing: Simulate a large number of concurrent user requests to verify the system’s concurrent processing capabilities. |
| § | Disaster Recovery Testing: Check if the system can still provide basic functions in the event of a real disaster. |
| § | Recovery Testing: Simulate unexpected situations to verify the system’s running state after backup recovery. |
| ● | Automated Testing |
| o | Build Automated Testing Framework: Introduce tools like Selenium, Appium, etc., to build a scalable automated testing framework. |
| o | Automate Performance Testing: Use professional tools like LoadRunner, JMeter, etc., to achieve automated performance testing. |
| o | Automate Functional Testing: Write automated scripts to cover different levels of functional testing such as UI/services/API. |
25
| o | Continuous Integration and Continuous Testing: Achieve seamless integration of automated testing into continuous integration/delivery pipelines. |
| o | Automated Test Report Generation: After testing, the system automatically generates detailed test reports, including results, logs, etc. |
| ● | Test Management Tool Integration |
| o | Defect Management Tools: Integrate defect management tools (like Jira) to efficiently track and record the defect lifecycle. |
| o | Test Case Management Tools: Import test case management tools (like Xray) to realize version control and reuse of cases. |
| o | Test Coverage Statistics: Automatically collect code and functional point test coverage through tools (like SonarQube). |
| o | Test Process Control: Use workflow tools (like TestRail) to standardize the management and tracking of test activities. |
| o | Test Data Management: Establish a test data management system to ensure the accuracy and reusability of test data. |
Deployment and Transition
| ● | Deployment Preparation Phase |
| o | Prepare Production Environment Infrastructure (servers, network, storage, etc.): We will evaluate and plan your existing IT infrastructure to ensure it meets the computational, storage, and network resource requirements of CRMAI. If necessary, we will provide expansion suggestions. |
| o | Build Pre-Deployment Environment: We will create an internal simulation environment highly similar to the production environment for pre-deployment testing and validation to minimize post-deployment risks. |
| o | Prepare Deployment Scripts, Tools, and Release Packages: Our deployment team will develop automated deployment scripts and prepare tested and version-controlled CRMAI release packages. |
| o | Prepare Configuration Data and Baseline Data: We will assist you in sorting out existing configuration data and business baseline data to ensure consistency in the new system. |
| o | Perform Security and Compliance Checks: Before deployment, we will conduct comprehensive security and compliance reviews to ensure it meets regulatory requirements. |
| ● | Deployment Verification Phase |
| o | Verify Release Package and Deployment Process in Pre-Deployment Environment: We will repeatedly verify the deployment process in the simulation environment and fix any issues found. |
26
| o | Perform System Integration Testing and End-to-End Testing: We will closely cooperate with your business team to ensure seamless integration of CRMAI with existing systems and processes. |
| o | Perform Performance and Load Testing: By simulating real business scenarios, we will verify the system’s performance under various load conditions. |
| o | Fix Issues and Rebuild Release Package: Once any issue is found, we will promptly fix it and rebuild the release package to ensure it meets go-live requirements. |
| ● | Go-Live Release Phase |
| o | Determine Go-Live Window and Notify Relevant Personnel: We will coordinate with you to select an appropriate go-live window and notify all relevant personnel to prepare. |
| o | *Execute System Deployment (application, data, configuration, etc.):** Once conditions are ready, we will deploy the CRMAI system in the production environment. |
| ● | Verify Release Results, Check Version and Configuration: After deployment, we will comprehensively verify the system version and configuration to ensure consistency. |
| ● | Switch Traffic and Access Entrances: With your consent, we will switch business traffic to the new system and update related access entrances. |
| ● | Transition Process Management |
| o | Develop Transition Plan and Procedures: We will formulate detailed transition plans and procedures in advance to minimize risks during the transition. |
| o | Establish Transition Process Monitoring and Early Warning Mechanism: During the transition, we will monitor key indicators in real time and establish an early warning mechanism. |
| o | Prepare Transition Rollback Plan: To reduce risks, we will prepare a transition rollback plan in advance to ensure business continuity. |
| o | Maintain Emergency Repair Team During Transition: We will keep an emergency repair team on standby to promptly handle any issues that arise during the transition. |
| ● | Post-Transition Check Phase |
| o | Verify Core Business Functions: Once the transition is complete, we will verify all core business functions of CRMAI together with your team. |
| o | Check Consistency of Key Data: We will check the consistency of key business data in the new system. |
27
| o | Monitor Key System Indicators: For a period after the transition, we will continuously monitor the key operating indicators of the system. |
| o | Address Post-Transition Issues: If any issues are found, we will promptly communicate with you and take appropriate remedial measures. |
| ● | Post-Transition Continuous Optimization Phase |
| o | Collect and Analyze Feedback and Operational Data: We will collect and analyze feedback and operational data from various parties. |
| o | Continuously Optimize System Performance and User Experience: Based on feedback, we will continuously optimize system performance and improve user experience. |
| o | Update System Operation Documentation and Knowledge Base: We will update the operation documentation and knowledge base to ensure that the system documentation remains current. |
| o | Initiate the Next Iteration Cycle: After the deployment work is complete, we will initiate a new iteration cycle to continuously optimize and improve the system. |
Implementation Scope:
| ● | Hardware Equipment Procurement: |
| o | AWS (Amazon Web Services): |
| § | Instance Types: We will evaluate your computational needs and recommend appropriate EC2 instance families and sizes, such as general-purpose (M5), compute-optimized (C5), or memory-optimized (R5), etc. |
| § | Storage: Based on data volume and access patterns, we can configure EBS cloud disks, EFS file systems, or S3 object storage for you. |
| § | Network: We will design a reasonable VPC network topology covering public subnets, private subnets, NAT gateways, etc., to ensure security and reliability. |
| § | Other Services: Use core AWS services like load balancing, auto-scaling, CloudWatch monitoring, etc., as needed. Use Google cloud products like Cloud SQL, Cloud Bigtable, Kubernetes Engine, etc., as needed. |
| ● | Basic Software Procurement: |
| o | OpenAI: |
| § | API Integration: We will evaluate the text generation, comprehension, translation, and other APIs provided by OpenAI and seamlessly integrate them into the customer interaction links of CRMAI. |
28
| § | Voice Model: Use the GPT language model for natural language processing and generation to enhance customer experience. |
| § | Custom Models: If needed, we can work with OpenAI to customize industry AI models based on your data. |
| o | Development Framework: |
| § | Frontend: Modern web frameworks like React, Vue. |
| § | Backend: Mature server-side frameworks like Spring Boot, Node.js. |
| § | Database: Relational databases, MongoDB. |
| § | Message Queues: Distributed message queues like RabbitMQ. |
| o | DevOps Toolchain: |
| § | Continuous Integration (CI): Automated build tools like Jenkins. |
| § | Containerization: Docker and container orchestration tools like Kubernetes for portable application deployment. |
| § | Monitoring Solutions: Prometheus open-source monitoring and visualization tools. |
| ● | System Environment Setup |
| o | Hardware Environment: |
| Component | Configuration | Description | ||
| Compute Resources | AWS EC2 c5.4xlarge or Google Cloud Compute Engine equivalent | 16vCPU, 32GB memory, scalable instance number | ||
| Kubernetes Cluster | Main Node: m5.xlarge (4vCPU, 16GB) | Working Node: c5.2xlarge (8vCPU, 16GB) | ||
| Storage | Object Storage AWS S3 | Static resources, logs, backup storage | ||
| File Storage | AWS EFS | Shared file system for applications | ||
| Database Storage | AWS RDS | Initial 1TB scalable, general-purpose SSD, multi-AZ deployment for high availability | ||
| Network | Private Cloud Environment AWS VPC | Load Balancing AWS: CLB/ALB/NLB | ||
| Security Control | Firewalls, security groups, etc., access control policies | |||
| Monitoring and Logs | Cloud Monitoring Service AWS CloudWatch | Logging System ELK or self-built logging system | ||
| Disaster Recovery | Cross-region deployment for disaster recovery backup | Cloud storage replicated backup data | ||
| Disaster Recovery Services | AWS CloudEndure or cloud vendor disaster recovery services |
29
| o | Operating System: |
| § | Use stable CentOS distribution as the server operating system. |
| o | Database: |
| § | Deploy relational databases like MySQL for storing customer data, transaction records, product information, and other structured data. |
| § | Possibly use NoSQL databases (such as MongoDB) to store unstructured data like knowledge base content, documents, etc. |
| § | Optimize the database based on data volume and query patterns, including table structure design, indexing, sharding, etc. |
| o | Web Server: |
| § | Install web server software like Nginx for deploying web applications. |
| § | Configure SSL/TLS encryption, load balancing, and other functions as needed. |
| o | Application Environment: |
| § | Set up the runtime environment for the programming language, including Java, Python, Node.js, etc. |
| § | Install the required web frameworks, libraries, and middleware. |
| o | Caching Services: |
| § | Consider using caching services like Redis to improve system response speed. |
| o | Message Queues: |
| § | Possibly use message queue services like RabbitMQ for asynchronous processing and decoupling. |
| o | Monitoring and Logs: |
| § | Deploy Prometheus monitoring tools to monitor system operating status. |
| § | Use ELK Stack log collection and analysis tools. |
| o | Third-Party Integration: |
| § | Integrate the system with existing Excel. |
30
| o | Security: |
| § | Configure firewall, intrusion detection, and other security measures. |
| § | Implement user authentication and access control mechanisms. |
| o | Continuous Integration/Continuous Delivery (CI/CD): |
| § | Establish CI/CD pipeline to achieve automated build, testing, and deployment. |
System Implementation (Requirement Sorting, Design, Development, Testing, Deployment)
| ● | Requirement Sorting |
| o | Communicate deeply with business departments and end-users to comprehensively sort out system requirements. |
| o | Review, classify, and prioritize requirements. |
| o | Formulate requirement documents, including functional requirements, non-functional requirements, integration requirements, etc. |
| ● | Design |
| o | Perform system architecture design based on requirement documents and determine technical selection. |
| o | Design database structures, data models, and API interfaces. |
| o | Design user interface (UI) and user experience (UX). |
| o | Write design documents such as architecture design documents, database design documents, UI/UX design documents, etc. |
| ● | Development |
| o | Perform system development according to design documents, including frontend, backend, and database, etc. |
| o | Follow coding standards to write high-quality, maintainable code. |
| o | Perform unit testing and integration testing to ensure code quality. |
| o | Integrate development with third-party systems (such as Advent Black Diamond and Suite8). |
| ● | Testing |
| o | Develop test plans, including test strategies, test cases, and test environments. |
| o | Perform functional testing, performance testing, security testing, etc., to ensure the system meets requirements and quality standards. |
| o | Perform user acceptance testing (UAT) with end-users to confirm the system meets expectations. |
| o | Write test reports to record test results and discovered defects. |
31
| ● | Deployment |
| o | Prepare the production environment, including hardware, operating system, middleware, etc. |
| o | Deploy applications and databases, configure related parameters. |
| o | Perform system integration testing to verify the normal operation of the production environment. |
| o | Formulate go-live plans, including data migration and transition strategies, etc. |
| o | Perform go-live operations and monitor the system’s running status. |
| o | Write deployment documents to record the deployment process and configuration information. |
| ● | Operation and Maintenance |
| o | Establish system monitoring and log analysis mechanisms to continuously monitor the system’s operating status. |
| o | Formulate fault emergency plans to quickly respond to and resolve system faults. |
| o | Continuously optimize and upgrade the system based on business needs and feedback. |
| o | Perform system backup and recovery strategies to ensure data security. |
| ● | Data Migration |
| Stage | Key Steps | |
| Data Assessment and Preparation | Evaluate existing data sources, Establish data cleansing rules, Design target database schema | |
| Data Migration Plan | Select incremental or full migration mode, Use data migration platform or integration tools, Synchronize new data in real-time/batch | |
| Execute Data Migration | Test migration in simulated environment, Refine migration rules and processes, Determine and execute final migration window | |
| Data Validation and Processing | Validate data after migration, Remedy for abnormal data, Establish data quality monitoring | |
| Data Access Permission Management | Establish permission control policies, Assign appropriate data operation permissions, Configure audit log recording |
32
System Pilot Operation
| ● | Functional Testing: Design corresponding test cases for each functional module listed in the document to comprehensively test each module’s various functional scenarios and ensure that the functions meet the requirements and run stably. |
| ● | Performance Testing: Conduct stress tests on the system’s response speed, concurrent users, data processing capabilities, etc., to evaluate the system’s performance under various workloads and identify potential bottlenecks. |
| ● | Compatibility Testing: Test the system’s compatibility in different environments, such as different operating systems, browsers, mobile devices, etc., to ensure the system can adapt to various usage scenarios. |
| ● | User Experience Testing: Invite sample users to try out the system, evaluate the system’s usability, ease of use, and user-friendliness, collect user feedback, and optimize the user experience. |
| ● | Data Migration Testing: If historical data needs to be migrated from the old system, test the completeness and accuracy of the data migration. |
| ● | Integration Testing: Test the system’s integration with other third-party systems (such as external links mentioned in the document) to ensure seamless data exchange and business process integration. |
| ● | Security Testing: Perform system penetration testing, vulnerability scanning, etc., to evaluate the system’s security protection capabilities and timely fix security vulnerabilities. |
| ● | Documentation and Training: Prepare operation manuals, online help, and training materials to ensure users can proficiently use the new system. |
Employee Training
| ● | Training Targets: Clearly define which employees of different roles and functional departments will receive training, and tailor the training content based on their job responsibilities. Typically includes sales staff, customer service staff, marketing staff, managers, etc. |
| ● | Training Content: The training content should cover the various functional modules of the system, including customer management, marketing activities, sales processes, report analysis, contract management, project management, etc., to ensure employees are familiar with the relevant modules’ operating procedures. Additionally, it should cover system integration, data security, best practices, and other common themes. |
| ● | Training Forms: Various forms of training can be adopted, including classroom training, online courses, video tutorials, hands-on operational guidance, etc., to suit different employees’ learning preferences and schedules. |
| ● | Training Materials: Prepare detailed training manuals, operation guides, case studies, etc., as classroom teaching and subsequent reference materials. These materials should be easy to understand, with rich illustrations. |
33
| ● | Assessment and Certification: Establish corresponding assessment mechanisms to ensure employees have a thorough understanding and mastery of the system. Set theoretical and practical assessments and issue certification certificates to employees who pass the assessment. |
| ● | Continuous Training: Since system functions will be continuously updated and iterated, establish a continuous training mechanism to provide employees with new feature training regularly and adjust training content based on employee feedback. |
| ● | Super Users: Cultivate a group of “super users” in each department who are not only proficient in system operations but also act as internal trainers and system promoters within the department, providing guidance and support to other employees. |
| ● | Training Effect Evaluation: Design training satisfaction surveys and subsequent performance assessments to evaluate the actual effect of training and provide improvement suggestions for subsequent training. |
Project Management, Quality Control
| ● | Project Management: |
| o | Project Organization: Clearly define the roles and responsibilities of key personnel such as project managers, technical leaders, test leaders, and module leaders, and establish an efficient project organization structure. |
| o | Project Schedule Management: Formulate a reasonable project schedule plan, reasonably allocate the workload of the project to various stages and milestones. Use project management software (such as the “project” function module mentioned in the document) to track project progress, timely discover and solve problems. |
| o | Risk Management: Identify risk factors that may affect the project’s progress, quality, and cost in advance and formulate corresponding risk mitigation measures, such as scope control, resource allocation, coordination, and communication, etc. |
| o | Change Management: Establish change control processes to strictly review requirements changes, design changes, etc., to control project scope expansion. |
| o | Communication Management: Regularly hold project meetings to promptly communicate progress, coordinate resources, and resolve cross-team issues. Also, strengthen communication with customers to timely obtain feedback. |
| o | Milestone Review: At the end of each stage, organize milestone review meetings to evaluate work completion, review deliverable quality, and determine whether to enter the next stage. |
34
| ● | Quality Control: |
| o | Quality System Construction: Establish a comprehensive quality management system, formulate quality plans, quality measurement standards, quality activities, and embed quality awareness throughout. |
| o | Requirement Review: Review requirement specification documents to identify problems such as omissions, contradictions, and ambiguities in requirements to ensure requirement quality. |
| o | Design Review: Review system design documents, database designs, user interface designs, etc., to identify design defects and control design quality. |
| o | Code Review: Conduct peer reviews of core function codes, shared component codes, etc., to improve code quality and maintainability. |
| o | Test Management: Complete different levels of testing activities such as unit testing, integration testing, system testing, acceptance testing, etc., according to the test strategy to ensure the delivered system meets quality requirements. |
| o | Defect Management: Establish a defect tracking system to record, analyze, track, and verify all discovered defects to ensure defects are effectively fixed. |
| o | Measurement Analysis: Collect various quality measurement data such as defect density, test coverage, etc., analyze quality trends, and continuously improve quality management activities. |
| o | Process Audit: Regularly audit the compliance of key process areas such as requirement management, testing, and change control in project execution. |
Operational Scope:
| ● | System Operation and Maintenance Support |
| o | Daily Monitoring: Set up system health monitoring to track CPU, memory, disk, network, and other resource usage to ensure system stability. |
| o | Fault Handling: Establish fault reporting and handling processes to quickly locate and resolve system faults, minimizing system downtime. |
| o | Backup and Recovery: Formulate data backup strategies and plans to regularly back up system data to ensure data security and timely recovery when needed. |
35
| o | Security Management: Perform security patch upgrades, strengthen system security protection, prevent malicious attacks, and ensure data and system security. |
| o | User Support: Provide 24/7 technical support hotline to promptly respond to and resolve user feedback issues. |
| ● | System Optimization |
| o | Performance Tuning: Continuously monitor system performance bottlenecks, optimize database, application server, and other system configurations, and improve system concurrent processing capabilities and response speed. |
| o | Function Improvement: Continuously improve and enhance system functions based on user feedback to improve user experience and meet business development needs. |
| o | Version Upgrade: Track CRMAI system version releases, timely plan and execute version upgrades to keep the system in the latest functional and secure state. |
| o | Capacity Planning: Evaluate and expand system storage, computing, and other resources based on business growth to prepare for continuous business growth. |
| ● | Others |
| o | Operation and Maintenance Automation: Research and introduce operation and maintenance automation tools to achieve automated monitoring, deployment, backup, etc., to improve operation and maintenance efficiency. |
| o | Knowledge Base Construction: Continuously summarize and improve the operation and maintenance knowledge base to provide reference and guidance for subsequent operation and maintenance work. |
| o | Training and Skill Improvement: Organize regular training for operation and maintenance personnel, update operation and maintenance knowledge and skills, and keep up with technology development trends. |
2. Project Overview and Requirements Analysis
2.1 Functional Requirements Analysis
Basic Modules:
| ● | Home Page (Home): The system entrance provides a portal for quick access to commonly used functional modules. It includes personalized layout and to-do items. |
| ● | Calendar: Schedule and time management, supporting personal, team, and resource calendars, schedule reminders, and recurring activities. |
36
| ● | Documents: Document center supports uploading, downloading, version control, folder classification, and full-text search document management functions. |
| ● | Emails: Integrated email system can send and receive emails, manage contacts, and email lists. |
Customer Management Module:
| ● | Customer Experience and Communication: Records customer interaction history, manages customer information, contacts, accounts, etc., providing a 360-degree customer view. Automates customer service processes. |
| ● | Potential Customers: Manages potential customer information, including source, contact information, communication records, and conversion opportunities. |
| ● | Potential Customer Lists: Dynamically manages filtered potential customer lists for easy marketing and sales follow-up. |
| ● | Application Effect: As the core module of the solution, the customer management module provides institutions with full lifecycle customer resource management capabilities. From customer profiling and segmentation to marketing expansion, relationship maintenance, and performance appraisal and incentives, the customer management module runs throughout, helping institutions fully explore customer value, provide personalized services, formulate precise marketing strategies, and control marketing performance. Ultimately, this module helps maintain customer assets and maximize their value. The modular design makes functions customizable to meet the diverse needs of institutions of different scales, making it an important part of the digital transformation of wealth management. |
Marketing Module:
| ● | Marketing Campaigns: Full process management of marketing campaign planning, execution, and effectiveness analysis, including campaign planning, promotional materials, lead management, etc. |
| ● | Events: Manages the organization, registration, check-in/check-out, and follow-up of events/meetings. |
| ● | Event Locations: Manages event location resource information. |
| ● | Application Effect: The marketing module supports institutions in accurately reaching potential customers. It integrates data analysis, customer profiling, marketing automation, etc., helping institutions deeply analyze market dynamics and customer needs, target high-value customer groups, and develop personalized marketing strategies and campaign plans. Through intelligent marketing channel management, the module can achieve unified delivery and multi-channel coverage of marketing content, significantly improving the precision and reach of marketing efforts. Additionally, the module provides full-chain marketing effectiveness analysis, realizing visualized management of input and output to continuously optimize marketing strategies. With the support of the marketing module, wealth management institutions can greatly improve marketing conversion rates, effectively expand high-value customers, and inject new momentum into business growth. |
37
Sales Module:
| ● | Call Records: Records and manages phone interactions with customers. |
| ● | Meetings: Schedules and records meetings with customers, including meeting topics, attendees, and minutes. |
| ● | Tasks: Creates, assigns, tracks, and manages tasks. |
| ● | Notes: Records text notes of interactions with customers. |
| ● | Invoices: Issues and manages customer invoices. |
| ● | Contracts: Full process management of contract drafting, review, signing, and archiving. |
| ● | Cases: Standardized management of customer issues/complaints/requests. |
| ● | Application Effect: The sales module provides financial advisors with efficient marketing support and customer service tools. It covers the entire process from lead acquisition to sales, including lead distribution, product sales, order management, and commission settlement, significantly improving sales efficiency and service quality. In terms of lead acquisition, the module is deeply integrated with the marketing module to achieve automated lead distribution, ensuring timely and precise follow-up of potential customers. Through the mobile client, financial advisors can grasp customer dynamics anytime and anywhere, carrying out precise and effective marketing interactions. In the sales service stage, the module provides product sales tools and a customer manager workbench, supporting personalized financial plan design, product configuration, and order processing to provide customers with a consistent and high-quality service experience. Order information is automatically transmitted to the back-end system, achieving process automation and avoiding manual processing errors. Additionally, the module features advanced functions such as commission distribution and compliance review, providing data support for sales assessment and risk control, making the sales process more standardized and efficient. Through the sales module, wealth management institutions can accelerate marketing conversions, improve customer service quality, and effectively expand market share, promoting continuous business growth. |
38
Project Management Module:
| ● | Projects: Full lifecycle management of projects, including tasks, resources, schedules, budgets, risks, etc. |
| ● | Project Templates: Project template library to speed up project initiation. |
| ● | Application Effect: The project management module provides institutions with efficient collaboration and process control capabilities, ensuring high-quality delivery of various financial service projects. It covers the entire project lifecycle, including demand management, planning, resource allocation, progress monitoring, risk control, quality management, and other key aspects, providing project managers with a one-stop collaboration platform and management tools. In the initial phase of the project, the module supports the standardized recording and decomposition of customer needs, assisting in the formulation of detailed work plans and resource arrangements, laying the foundation for project implementation. In the execution phase, multi-dimensional progress dashboards and reports can monitor project progress in real-time, automatically identify potential risks, and help project managers make timely adjustments to ensure on-time project delivery. The project management module is seamlessly integrated with other wealth management solution modules, efficiently sharing customer information, product data, transaction data, etc., providing timely and reliable support data for project personnel to improve work efficiency and decision quality. With the support of the project management module, wealth management institutions can enhance the standardization and standardization level of financial services, shorten project delivery cycles, reduce communication costs, and ultimately provide customers with better and more efficient financial consulting and portfolio management services. |
Product Module:
| ● | Products: Manages company product/service information, pricing, inventory, etc. |
| ● | Product Categories: Manages the product classification system. |
| ● | Application Effect: The product module provides institutions with unified product data management and decision support capabilities, ensuring the optimal financial product portfolio for customers. The module builds a unified product data center, centrally managing comprehensive data on various financial products in the financial market, such as stocks, funds, insurance, trusts, etc., including basic information, risk ratings, historical performance, etc., providing a data foundation for product selection and optimization. The built-in product evaluation and analysis model can automatically calculate core indicators such as product yield and risk value, and combined with product liquidity, cost, and tax factors, tailor a product rating system and configuration strategy for financial managers, significantly improving investment portfolio optimization efficiency. At the same time, the module provides product account integration and net value revaluation functions, which can automatically collect and calculate the real-time net value situation of customer portfolios, providing data support for timely adjustment of operational strategies. Through the product module, wealth management institutions can efficiently manage massive product data, master advanced analysis and decision-making tools, reasonably allocate and dynamically optimize investment portfolios according to customer risk preferences, maximally meet customers’ financial needs, and improve overall investment return rates. |
39
Reporting and Analysis Module:
| ● | Portfolio Management and Reporting: Tracks and manages investment product/service portfolios. |
| ● | Business Intelligence and Compliance: Provides visual business indicator systems, supporting multi-dimensional data analysis. |
| ● | Reports: Pre-made and customizable operational reports and analytical reports. |
| ● | Application Effect: The reporting and analysis module provides data-driven analytical insights for institutional business management and investment decision-making. This module deeply integrates the full-chain data of wealth management business, including customer information, marketing activities, financial products, investment portfolios, project management, etc., through modeling and analysis, forming multi-dimensional reports and visual screens to provide decision-makers with comprehensive business insights. In terms of business operations, the module sets up automatic statistical analysis mechanisms for key performance indicators, such as customer development efficiency, product sales rankings, marketing expense return rates, etc., and supports multi-dimensional data drilling, helping management quickly identify business highlights and issues. In terms of investment management, the module integrates advanced quantitative analysis models to perform multi-scenario simulation calculations on customer portfolios, product returns, risk exposure, etc., assisting investment managers in scientifically evaluating risk and return to develop forward-looking investment strategies. Additionally, the module provides self-service reporting tools and open APIs, facilitating each department’s independent data analysis and application development based on needs, improving the flexibility and practicality of the analysis module. With the support of the reporting and analysis module, wealth management institutions can truly achieve data-driven decision-making, instantly grasp business operation status and portfolio performance, and continuously optimize business and investment strategies based on analytical results, gaining an advantage in industry competition. |
Integration Module:
| ● | Partners and Integration: Data integration and business collaboration with third-party application systems. |
| ● | Application Effect: This module provides a standardized integration framework and interface specifications, supporting bidirectional integration with core transaction systems, customer relationship management systems, financial systems, and other third-party application systems to achieve real-time data exchange and automatic business process transmission, eliminating data silos and avoiding inefficiency and errors caused by duplicate entry. |
In terms of data integration, the module adopts a distributed data bus architecture to achieve cross-system, cross-platform data exchange in a high-performance, high-reliability manner, ensuring consistency and real-time availability of key business data throughout the process, providing accurate data support for decision analysis and operational control.
In terms of business integration, the module follows the principle of service-oriented architecture, packaging the core functions of each system into services, and through business process orchestration, it can flexibly assemble new business processes across systems, such as automated credit checks, risk control approvals, and transaction reconciliations, significantly improving business collaboration efficiency and user experience.
Additionally, the module provides monitoring and reporting functions to track integration health status in real-time, promptly identifying and resolving integration issues to ensure stable and efficient system integration operations.
With the support of the integration module, wealth management institutions can break through system data and business barriers, achieve full-process collaboration and automation, not only improving internal operational efficiency but also providing high-quality one-stop service experiences for customers.
40
Knowledge Base Module:
| ● | Knowledge Base: Enterprise internal knowledge article library. |
| ● | Knowledge Base Categories: Knowledge article classification system. |
| ● | Application Effect: The knowledge base module provides employees with a systematic knowledge management and learning platform, helping institutions improve professional service capabilities. This module builds a unified knowledge base, covering various fields of financial management, such as macroeconomics, investment strategies, product analysis, and legal compliance, centrally managing the professional knowledge resources accumulated within the institution and industry information acquired externally, ensuring the authority, accuracy, and timeliness of knowledge. The knowledge base provides intelligent knowledge retrieval and push mechanisms, allowing employees to obtain personalized knowledge services based on their roles and work content, efficiently acquiring the necessary professional knowledge and shortening the learning curve. The module supports mobile knowledge browsing, enabling learning anytime and anywhere. The module also includes knowledge assessment and training management functions, allowing institutions to set knowledge points and passing standards based on different positions and levels, guiding employees to continuously learn and improve. Training resources can also be managed and pushed uniformly, improving training quality and participation. With the support of the knowledge base module, wealth management institutions can enhance the management and utilization of core knowledge assets, improve employees’ professional literacy, provide customers with more professional and targeted financial advice and investment suggestions, thereby winning customer trust and favor, and promoting long-term business development. |
Others:
| ● | PDF Templates: Customizable PDF templates, such as contracts, invoices, reports, etc. |
| ● | Email Templates: Customizable email templates for automated personalized email sending. |
| ● | Surveys: Online survey design, publishing, and statistical analysis. |
2.2 Non-Functional Requirements Analysis
Performance Requirements:
| ● | Response Time: Interface loading <2 seconds, data query <5 seconds. |
| ● | Concurrent Users: Supports 1000+ concurrent online users. |
| ● | Capacity: Supports storing 1TB+ data, scalable. |
Availability Requirements:
| ● | Availability Goal: 99%. |
| ● | Fault Recovery Target Time: Critical functions recovered within 4 hours. |
| ● | Online Maintenance: Supports online upgrades, backups, and other maintenance operations. |
41
Security Requirements:
| ● | Access Control: Role-based permission management. |
| ● | Data Encryption: High-strength encryption for sensitive data such as passwords and payment information. |
| ● | Audit Trail: Key operations are traceable for auditing. |
| ● | Attack Prevention: Equipped with firewall, anti-DDoS, and anti-SQL injection security protection. |
Maintainability Requirements:
| ● | Modular Design: High cohesion, low coupling. |
| ● | Standardized Coding: Adheres to coding standards. |
| ● | Comprehensive Documentation: Requirements, design, testing, and other documentation. |
| ● | Software Deployment: Standardized and automated software release process. |
Scalability Requirements:
| ● | Distributed Deployment: Based on microservice architecture, horizontally scalable. |
| ● | Containerization: Supports containerized deployment. |
| ● | Pluggable Modules: Third-party applications/services can be integrated. |
Compatibility Requirements:
| ● | Browser Compatibility: Supports the current and previous two versions of major browsers. |
| ● | Mobile Compatibility: Adapts to mainstream mobile systems and resolutions. |
| ● | System Integration: Supports integration with existing enterprise systems. |
Internationalization Requirements:
| ● | Multilingual: Supports localization for 12 languages. |
| ● | Currency Formats: Supports 40+ currency formats. |
| ● | Data Formats: Supports various formats such as time zones, dates, and numbers. |
42
Legal Compliance Requirements:
| ● | Data Protection: Complies with regulations such as GDPR and CCPA. |
| ● | Accessibility: Conforms to WCAG 2.1 accessibility standards. |
| ● | Industry Compliance: Meets relevant regulatory requirements in the financial sector. |
Human-Computer Interaction Requirements:
| ● | User-Friendly Interface: Intuitive and consistent UI design philosophy. |
| ● | Assistive Features: Provides shortcuts, personalized settings, etc. |
| ● | Help Documentation: Contextual online help documentation. |
Intelligence Requirements:
| ● | Intelligent Recommendations: Provides marketing activity recommendations based on AI analysis. |
| ● | Natural Language Processing: Supports natural language query data. |
| ● | Machine Learning: Continuously optimizes various business decision models. |
2.3 Other Requirements Analysis
Integration Requirements:
| ● | Data Integration: Can integrate data bidirectionally with existing enterprise systems (e.g., ERP, email servers). |
| ● | Application Integration: Provides standardized API interfaces to support integration with third-party application systems. |
| ● | Data Migration: Smooth migration of historical data from the old system to the new system. |
Deployment Requirements:
| ● | Cloud Deployment: Supports public cloud, private cloud, and hybrid cloud deployment modes. |
| ● | Local Deployment: Can be deployed and maintained locally in the enterprise data center. |
| ● | Containerization: Uses container technologies like Docker for agile deployment. |
Monitoring Requirements:
| ● | System Monitoring: Comprehensive monitoring of CPU, memory, disk, network, and other resource usage. |
| ● | Log Monitoring: Collects and analyzes various logs such as system, application, security, and audit logs. |
| ● | Alarm Notification: Timely notifies operations personnel when exceptions occur. |
43
Backup Requirements:
| ● | Data Backup: Regularly performs complete backups of data according to preset strategies. |
| ● | Application Backup: Supports backup of system program files, configurations, etc. |
| ● | Backup Recovery: Can quickly restore data and applications from backups. |
Business Continuity Requirements:
| ● | Disaster Recovery: Provides data and application backups through a remote disaster recovery center. |
| ● | Fault Tolerance: Automatically switches to backup systems when the main system fails. |
| ● | Load Balancing: Distributes traffic to multiple server instances, improving availability. |
Testing Requirements:
| ● | Test Coverage: 100% functional testing coverage, including unit, integration, system, and acceptance testing. |
| ● | Automation: Achieves continuous integration and continuous testing through an automated testing framework. |
| ● | Test Environment: Independent test environment separated from the production environment. |
Documentation Requirements:
| ● | Requirement Documentation: Fully reflects business and system requirements. |
| ● | Design Documentation: Architecture, modules, interfaces, database, and other design descriptions. |
| ● | User Manual: User guides for operation processes and interface explanations. |
| ● | Online Help: Context-related built-in system help documentation. |
44
Training Requirements:
| ● | Administrator Training: Training for system management, maintenance, backups, etc. |
| ● | User Training: Usage training for different roles and business scenarios. |
| ● | Developer Training: Training on coding standards, development tools, environment setup, etc. |
III. Technical Implementation Plan
3.1 System Architecture Design
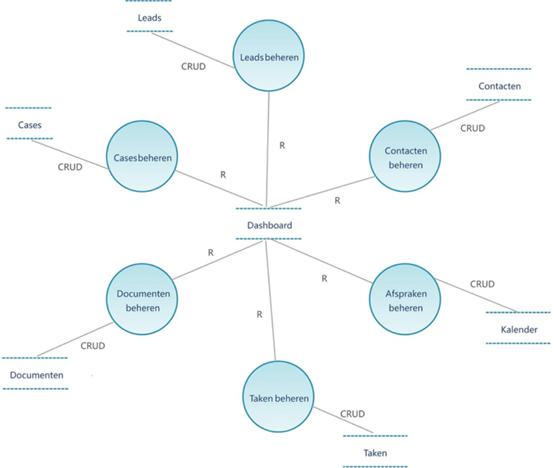
Frontend Architecture:
| ● | Single Page Application (SPA) architecture using modern frontend framework React. |
| ● | Follows component-based, modular design principles to improve code reusability. |
| ● | State management using libraries like Redux. |
| ● | Supports server-side rendering (SSR) to enhance first-screen loading speed. |
| ● | Introduces UI component libraries like Ant Design. |
45
Backend Architecture:
| ● | Microservice architecture, splitting the system into independent microservices. |
| o | Customer service, marketing service, contract service, knowledge base service, etc. |
| o | Implemented based on Node.js/Java/Python languages. |
| ● | Each microservice is a standalone application, including control layer, service layer, and persistence layer. |
| ● | Service registration and discovery through Consul. |
| ● | Service communication using RESTful API and message queues (e.g., RabbitMQ). |
| ● | API gateway exposes services uniformly to the outside, implementing identity authentication, monitoring, rate limiting, etc. |
Data Layer:
| ● | Main database uses relational database MySQL. |
| ● | Uses NoSQL databases like MongoDB for specific scenarios. |
| ● | Uses ElasticSearch as a full-text search engine. |
| ● | Data caching uses Redis to improve read performance. |
Operations Architecture:
| ● | Containerized deployment, using Docker to package applications and dependencies into images. |
| ● | Container orchestration using Kubernetes, achieving elastic scaling, fault tolerance, etc. |
| ● | Continuous integration and delivery, based on Jenkins for code building, testing, and deployment. |
46
| ● | System monitoring implemented by components like Prometheus. |
| ● | Introduces Application Performance Monitoring (APM) like Jaeger to trace distributed service calls. |
| ● | Unified log collection to ELK (Elasticsearch, Logstash, Kibana). |
| ● | Based on Istio to achieve microservice traffic management, security control, etc. |
Security Architecture:
| ● | API gateway and identity authentication services achieve unified authentication and authorization. |
| ● | Uses OAuth2 protocol to protect resource access. |
| ● | Manages system permissions based on Role-Based Access Control (RBAC). |
| ● | Encrypts sensitive data storage using asymmetric encryption algorithms. |
| ● | Deploys on a Virtual Private Cloud (VPC) to implement network isolation and access control. |
| ● | Web Application Firewall (WAF) blocks common web attacks. |
Integration Layer:
| ● | Uses Enterprise Service Bus (ESB) to integrate third-party systems. |
| ● | Supports various integration methods: file transfer, database link, message queue, API, etc. |
| ● | Introduces integration platforms like Mulesoft to achieve low-code integration. |
3.2 Key Technology Selection
Frontend Frameworks and Technologies:
| ● | React: Uses React as the frontend framework, combined with Redux for state management. |
| ● | Ant Design: Uses Ant Design React UI component library to provide rich UI components. |
| ● | TypeScript: Introduces TypeScript to improve code maintainability. |
Backend Frameworks and Technologies:
| ● | Spring Boot/Spring Cloud: Uses Spring Boot to build microservices, and Spring Cloud provides service discovery, configuration management, etc. |
| ● | Netflix OSS: Uses Eureka as the service registry center, Zuul as the API gateway. |
| ● | RabbitMQ: Uses RabbitMQ as the message queue for asynchronous communication between microservices. |
47
Database and Cache:
| ● | MySQL: Uses MySQL as the relational database to store core business data. |
| ● | MongoDB: Uses MongoDB to store unstructured data with free format. |
| ● | Elasticsearch: Uses Elasticsearch as a full-text search engine to provide strong search capabilities. |
| ● | Redis: Uses Redis as a distributed cache to improve system read performance. |
Containers and Orchestration:
| ● | Docker: Uses Docker to package applications and dependencies into images. |
| ● | Kubernetes: Uses Kubernetes for container orchestration, achieving automated deployment, scaling, etc. |
Continuous Integration and Delivery:
| ● | Jenkins: Uses Jenkins as the continuous integration platform to achieve code scanning, building, testing, etc. |
| ● | Kubernetes: Combined with Kubernetes to achieve continuous deployment to test and production environments. |
Monitoring and Logs:
| ● | Prometheus: Uses Prometheus to monitor application running indicators. |
| ● | Grafana: Visually displays Prometheus monitoring data. |
| ● | ELK: Uses ELK (Elasticsearch, Logstash, Kibana) to collect, query, and analyze logs. |
Security and Integration:
| ● | Spring Security: Uses Spring Security to achieve authentication and authorization control. |
| ● | Keycloak: Uses Keycloak to centrally manage authentication and single sign-on. |
| ● | Apache Camel: Uses Camel as the Enterprise Integration Patterns (EIP) framework to integrate third-party systems. |
3.3 Functional Module Design
Home Page:
| ● | Description: Provides an overview of the system, including user activities, pending tasks, and quick access to frequently used functions. |
| ● | Functions: |
| o | Dashboard: Displays key business indicators and data visualizations. |
| o | Quick Access: Quickly accesses recently used modules and functions. |
| o | Notifications: Displays the latest messages and reminders within the system. |
48
Customer Experience and Communication:
| ● | Description: Supports interaction between customers and the company, enhancing the customer experience. |
| ● | Functions: |
| o | Real-Time Chat: Supports real-time communication between customers and customer service personnel. |
| o | Customer Feedback: Collects and analyzes customer feedback information. |
| o | Social Media Integration: Integrates customer interactions from various social media platforms. |
Portfolio Management and Reporting:
| ● | Description: Manages customers’ investment portfolios and generates related reports. |
| ● | Functions: |
| o | Portfolio Management: Tracks and manages customer portfolios. |
| o | Report Generation: Generates customized investment reports based on customer needs. |
| o | Risk Assessment: Performs risk analysis and assessment of portfolios. |
Business Intelligence and Compliance:
| ● | Description: Provides business intelligence analysis and compliance management. |
| ● | Functions: |
| o | Data Analysis: Uses data mining and analysis tools for business data analysis. |
| o | Compliance Checks: Ensures business operations comply with relevant regulations and standards. |
| o | Reporting and Auditing: Generates compliance reports and supports internal audits. |
Partners and Integration:
| ● | Description: Manages relationships with partners and supports integration with third-party systems. |
| ● | Functions: |
| o | Partner Management: Records and manages partner information. |
| o | System Integration: Integrates seamlessly with other business systems (e.g., ERP, HRM). |
| o | API Interface: Provides open API interfaces for third-party system calls. |
49
Calendar:
| ● | Description: Provides calendar functions for individuals and teams, supporting task and event management. |
| ● | Functions: |
| o | Event Scheduling: Creates and manages personal and team events. |
| o | Task Reminders: Sets task reminders to ensure timely completion of work. |
| o | Synchronization: Supports synchronization with other calendar systems (e.g., Google Calendar). |
Documents:
| ● | Description: Centralized management of various company and customer documents. |
| ● | Functions: |
| o | Document Upload and Storage: Supports uploading and storing various documents. |
| o | Permission Management: Sets access permissions for different users. |
| o | Version Control: Records document history versions, supporting version recovery. |
Emails:
| ● | Description: Manages email communication within the company and with customers. |
| ● | Functions: |
| o | Email Sending and Receiving: Supports sending and receiving emails. |
| o | Email Classification: Automatically classifies emails according to different rules. |
| o | Email Templates: Provides predefined email templates to enhance email sending efficiency. |
Marketing Campaigns:
| ● | Description: Manages and tracks various marketing activities of the company. |
| ● | Functions: |
| o | Campaign Creation: Creates and manages different types of marketing campaigns. |
| o | Data Analysis: Analyzes campaign effectiveness and provides detailed data reports. |
| o | Customer Segmentation: Conducts precise marketing based on customer characteristics. |
50
Call Records:
| ● | Description: Records and manages phone communications with customers. |
| ● | Functions: |
| o | Call Logging: Records all call information with customers. |
| o | Call Analysis: Analyzes call data to evaluate communication effectiveness. |
| o | Call Reminders: Sets call reminders to ensure important calls are not missed. |
Meetings:
| ● | Description: Manages meeting arrangements within the company and with customers. |
| ● | Functions: |
| o | Meeting Scheduling: Creates and manages meeting schedules. |
| o | Meeting Notes: Records meeting content and decisions. |
| o | Meeting Reminders: Sets meeting reminders to ensure timely attendance. |
Tasks:
| ● | Description: Manages and assigns various tasks within the company. |
| ● | Functions: |
| o | Task Creation: Creates and assigns tasks to different team members. |
| o | Task Tracking: Tracks task progress in real-time. |
| o | Task Reminders: Sets task deadline reminders. |
Notes:
| ● | Description: Records and manages various notes within the company. |
| ● | Functions: |
| o | Note Creation: Supports recording notes in various forms such as text and images. |
| o | Note Classification: Manages notes by different projects or themes. |
| o | Note Sharing: Supports sharing and collaboration of notes within the team. |
51
Invoices:
| ● | Description: Manages invoice information between customers and the company. |
| ● | Functions: |
| o | Invoice Generation: Generates invoices based on transaction information. |
| o | Invoice Sending: Supports sending invoices via email. |
| o | Invoice Tracking: Tracks the payment status and history of invoices. |
Contracts:
| ● | Description: Manages contracts between the company and customers or suppliers. |
| ● | Functions: |
| o | Contract Creation: Creates and manages contract templates and specific contracts. |
| o | Contract Review: Supports the approval and signing process of contracts. |
| o | Contract Archiving: Securely stores contract documents and supports query and retrieval. |
Cases:
| ● | Description: Manages and tracks customer service cases. |
| ● | Functions: |
| o | Case Creation: Records customer service requests and issues. |
| o | Case Assignment: Assigns cases to relevant team members for processing. |
| o | Case Tracking: Tracks case handling progress and results in real-time. |
Potential Customers:
| ● | Description: Manages and develops potential customers. |
| ● | Functions: |
| o | Customer Information: Records detailed information about potential customers. |
| o | Customer Rating: Rates potential customers based on their behavior and characteristics. |
| o | Customer Follow-Up: Formulates and tracks follow-up plans for potential customers. |
52
Potential Customer Lists:
| ● | Description: Filters and manages potential customer lists based on different criteria. |
| ● | Functions: |
| o | List Creation: Creates different potential customer lists based on customer characteristics. |
| o | List Analysis: Analyzes the effectiveness of potential customer lists. |
| o | List Export: Supports exporting potential customer lists in various formats. |
Projects:
| ● | Description: Manages and tracks various projects within the company. |
| ● | Functions: |
| o | Project Creation: Creates and manages project plans. |
| o | Project Assignment: Assigns project tasks to team members. |
| o | Project Tracking: Tracks project progress and outcomes in real-time. |
Project Templates:
| ● | Description: Provides predefined project templates to enhance project management efficiency. |
| ● | Functions: |
| o | Template Creation: Creates and manages project templates. |
| o | Template Application: Quickly applies existing templates to new projects. |
| o | Template Updates: Regularly updates and optimizes project templates. |
Events:
| ● | Description: Manages and organizes various company events. |
| ● | Functions: |
| o | Event Scheduling: Creates and manages event schedules. |
| o | Event Promotion: Promotes event information through various channels. |
| o | Event Feedback: Collects and analyzes feedback from event participants. |
53
Event Locations:
| ● | Description: Manages location information for company events. |
| ● | Functions: |
| o | Location Logging: Records specific location information for events. |
| o | Location Maps: Provides maps and route guides for event locations. |
| o | Location Management: Selects and reserves suitable locations based on event needs. |
Products:
| ● | Description: Manages various product information sold by the company. |
| ● | Functions: |
| o | Product Information: Records detailed information and specifications of products. |
| o | Product Pricing: Manages product pricing strategies and discount information. |
| o | Inventory Management: Monitors product inventory in real-time. |
Product Categories:
| ● | Description: Manages product classification based on different criteria. |
| ● | Functions: |
| o | Category Creation: Creates categories based on product characteristics. |
| o | Category Adjustment: Adjusts product categories based on market demand. |
| o | Category Analysis: Analyzes sales situations of various product categories. |
PDF Templates:
| ● | Description: Provides customizable PDF document templates. |
| ● | Functions: |
| o | Template Design: Designs PDF templates that align with the company’s image. |
| o | Template Application: Applies PDF templates to various reports and documents. |
| o | Template Management: Updates and maintains the PDF template library. |
54
Reports:
| ● | Description: Generates and manages various business reports. |
| ● | Functions: |
| o | Report Design: Designs different types of reports based on requirements. |
| o | Report Generation: Automatically generates regular reports. |
| o | Report Analysis: Analyzes report data to provide decision support. |
Knowledge Base:
| ● | Description: Centrally manages the company’s knowledge and information resources. |
| ● | Functions: |
| o | Knowledge Entry: Records and organizes internal knowledge information. |
| o | Knowledge Search: Provides fast and efficient knowledge search functions. |
| o | Knowledge Sharing: Supports knowledge sharing and collaboration within the team. |
Knowledge Base Categories:
| ● | Description: Manages the knowledge base classification system based on different criteria. |
| ● | Functions: |
| o | Category Creation: Creates categories based on knowledge content. |
| o | Category Adjustment: Adjusts knowledge categories based on needs. |
| o | Category Analysis: Analyzes the usage frequency and effectiveness of various knowledge categories. |
Email Templates:
| ● | Description: Provides predefined email templates to improve sending efficiency. |
| ● | Functions: |
| o | Template Design: Designs email templates that align with the brand image. |
| o | Template Management: Updates and maintains the email template library. |
| o | Template Application: Quickly calls templates during email sending. |
55
Surveys:
| ● | Description: Designs and manages various customer surveys. |
| ● | Functions: |
| o | Survey Creation: Designs surveys based on requirements. |
| o | Survey Sending: Sends surveys via email or other channels. |
| o | Survey Analysis: Collects and analyzes survey results to provide feedback reports. |
3.4 Integration Plan
Integration Architecture: Adopts a centralized integration architecture based on an Enterprise Service Bus (ESB), where all integrations with external systems are managed and implemented through the ESB. The ESB acts as the core integration layer, responsible for coordinating data exchange and business process orchestration among systems.
Integration Platform Selection: Choose MuleSoft Anypoint Platform as the integration platform, with the following advantages:
| ● | Cloud-native architecture, supports containerized deployment. |
| ● | Based on Mule ESB core, provides visual integration flow development. |
| ● | Supports numerous connectors, easily integrating various applications and systems. |
| ● | API management function, achieving the full lifecycle management of API design, testing, and publishing. |
| ● | Anypoint Exchange provides pre-built connector and template assets. |
| ● | High compliance and security, supporting OAuth, two-way SSL, etc. |
Integration Implementation:
| ● | Data Integration: Uses MuleSoft batch job connectors for data synchronization and ETL transformation. |
| ● | API Integration: Exposes application APIs through API gateway for other systems to call. |
| ● | Event-Driven Integration: Uses MuleSoft message queue connectors to interface with Kafka/RabbitMQ, supporting event-driven architecture. |
| ● | B2B Integration: MuleSoft B2B Connector supports multiple industry-standard protocols like EDI, AS2, etc. |
| ● | IoT Integration: Connects IoT devices, collects, and processes sensor data. |
Integration Scenarios Examples:
| ● | Integrating with CRM cloud marketing services to obtain marketing leads and campaign data. |
| ● | Integrating with electronic signature systems to support online contract signing. |
| ● | Integrating with identity authentication services to provide single sign-on functionality. |
56
Integration Governance:
| ● | API Management: Manages API lifecycle through Anypoint Platform’s API management functions. |
| ● | Integration Asset Management: Stores integration applications, rules, policies, and other assets in Anypoint Exchange asset library. |
| ● | Monitoring and Maintenance: Implements integration flow monitoring and fault recovery using MuleSoft’s Monitoring and Alerting functions. |
| ● | Security and Compliance: Anypoint Platform follows security best practices, supporting centralized control of security policies. |
3.5 Innovation Point Analysis
Intelligent Customer Experience:
| ● | Uses Natural Language Processing (NLP) technology to achieve intelligent voice assistants, allowing customers to interact in natural language. |
| ● | Applies machine learning algorithms to analyze customer data and provide personalized intelligent recommendations and services. |
| ● | Uses sentiment analysis technology to enhance customer experience by promptly resolving customer dissatisfaction issues. |
Intelligent Marketing and Sales:
| ● | Accurately markets and predicts potential sales leads based on customer data and behavior patterns. |
| ● | Applies machine learning analysis technology to optimize marketing campaign return on investment. |
| ● | Introduces natural language understanding to intelligently analyze the sentiment and opinions of marketing content. |
Intelligent Business Analysis:
| ● | Integrates big data analysis and data mining technologies to provide intelligent business analysis and reporting. |
| ● | Applies predictive analysis models to forecast and optimize business operations. |
| ● | Uses graph analysis technology for fraud detection and anti-money laundering monitoring. |
Intelligent Knowledge Management:
| ● | Uses natural language processing to extract valuable insights from the knowledge base. |
| ● | Applies knowledge graph association technology to discover potential associations between knowledge. |
| ● | Provides an automatic question-answering service based on the knowledge base using chatbots. |
57
Intelligent Compliance Management:
| ● | Uses machine learning to analyze transaction data and identify compliance risks. |
| ● | Automates audit processes to improve audit quality and efficiency. |
| ● | Conducts stress tests and risk assessments using machine learning models. |
No-Code Visual Development:
| ● | Provides a low-code development platform similar to Mendix for visual application development. |
| ● | Introduces a drag-and-drop PDF template designer for designing and publishing without coding. |
| ● | Supports automated integration and business process configuration on the platform. |
Open Ecosystem:
| ● | Provides standardized open interfaces based on microservices and API architecture. |
| ● | Builds a partner ecosystem, integrating third-party applications and services. |
| ● | Provides an app store and marketplace for discovering and distributing applications. |
58
| 4. | Project Implementation Plan |
| 4.1 | Project Organization Structure |
| ● | Project Sponsor: Responsible for the project’s initiation, funding, and final acceptance. Composed of senior company executives. |
| ● | Project Manager: Fully responsible for planning, executing, monitoring, controlling, and closing the project. |
| ● | Project Management Office (PMO): Provides consultation, training, and supervision to the project manager and team, ensuring consistency and effectiveness in project management practices. |
| ● | Core Project Team: Includes key roles such as system architect, technical lead, and testing lead, responsible for core work such as system design, development, and testing. |
| ● | Functional Development Teams: Divided into multiple development teams according to functional modules, each team composed of developers, testers, and business analysts, responsible for requirement analysis, design, development, and testing of corresponding modules. |
| ● | Quality Assurance Team: Independent of the development team, responsible for setting quality standards, reviewing quality-related processes, identifying quality defects, and proposing improvement measures. |
| ● | User Representatives: Representatives from different business departments, responsible for determining business requirements, reviewing design documents, and participating in user acceptance testing. |
| ● | Training Team: Responsible for providing system usage training to end users, ensuring users can proficiently use the new system. |
| ● | Technical Support Team: Provides support for system go-live and operation, responding to and resolving technical issues encountered by users in a timely manner. |
| 4.2 | Project Process |
Project Initiation Phase:
| ● | Establish the project management team and various working groups. |
| ● | Develop the project charter, clarifying project goals, scope, milestones, etc. |
| ● | Conduct a project kickoff meeting to inform all relevant personnel about the project. |
Requirement Analysis Phase:
| ● | Collect requirements from various business departments. |
| ● | Organize requirement review meetings to refine and confirm requirements. |
| ● | Write the requirement specification document. |
59
System Design Phase:
| ● | Conduct conceptual design and develop the overall system architecture. |
| ● | Design the database, user interfaces, reports, etc. |
| ● | Write the software design specification document. |
System Development Phase:
| ● | Assign functional modules to development teams for coding. |
| ● | Conduct code reviews and unit testing during the development process. |
| ● | Integrate all modules and conduct system testing. |
System Testing Phase:
| ● | Perform functional testing, integration testing, performance testing, etc. |
| ● | Track and fix defects. |
| ● | Conduct user acceptance testing (UAT). |
System Deployment Phase:
| ● | Determine system environment requirements. |
| ● | Execute the data migration plan. |
| ● | Deploy the system and conduct user training. |
Operation Support Phase:
| ● | Officially go live with the system and switch over. |
| ● | Develop an operation management plan. |
| ● | Continuously track user feedback and provide technical support. |
Project Monitoring Phase (Throughout the Project):
| ● | Develop a project quality management plan. |
| ● | Control project progress, risks, issues, and changes. |
| ● | Hold regular project meetings to summarize and adjust strategies. |
Project Closure Phase:
| ● | Officially close the project after achieving all milestones. |
| ● | Write a project summary report to capture lessons learned. |
| ● | Hold a project closure meeting to officially deliver the results. |
60
Work Breakdown Structure:
| Level 1 Task | Level 2 Task | Level 3 Task | Task Breakdown |
| Project Initiation | Project Definition & Planning | Project Goal Setting | |
| Project Scope Determination | |||
| Project Budget Preparation | |||
| Project Schedule Creation | |||
| Requirements Gathering & Analysis | User Requirements Survey | ||
| Requirements Documentation | |||
| Requirements Review & Confirmation | |||
| Feasibility Study | |||
| Project Team Building | |||
| Project Plan Creation | |||
| System Design | System Architecture Design | System Module Division | |
| Technology Selection | |||
| Architecture Diagram Creation | |||
| Database Design | |||
| Interface Design | |||
| Module Design | |||
| System Development | Front-end Development | Home Page Development | |
| Customer Experience & Communication Module | |||
| Calendar Module | |||
| Document Module | |||
| Email Module | |||
| Marketing Campaign Module | |||
| Phone Log Module | |||
| Meeting Module | |||
| Task Module | |||
| Notes Module | |||
| Invoice Module | |||
| Contract Module | |||
| Case Module | |||
| Leads Module | |||
| Lead List Module | |||
| Project Module | |||
| Project Template Module | |||
| Event Module | |||
| Event Location Module |
61
| Product Module | |||
| Product Category Module | |||
| PDF Template Module | |||
| Report Module | |||
| Knowledge Base Module | |||
| Knowledge Base Category Module | |||
| Email Template Module | |||
| Survey Module | |||
| Back-end Development | Database Setup & Optimization | Database Table Structure Design | |
| Index Optimization | |||
| Data Backup & Recovery Plan | |||
| API Development & Integration | |||
| Security Design & Implementation | |||
| System Integration | Portfolio Management & | ||
| Reporting Integration | |||
| Business Intelligence & Compliance Integration | |||
| Partner & Integration Module Development | |||
| Unit Testing | |||
| Integration Testing | |||
| System Testing | |||
| Testing & Validation | User Acceptance Testing (UAT) | Test Case Writing | |
| UAT Environment Setup | |||
| Test Execution & Feedback Collection | |||
| Production Environment Deployment | |||
| Data Migration | |||
| System Go-Live | |||
| Deployment & Release | User Training | Training Material Preparation | |
| Training Course Arrangement | |||
| User Training Implementation | |||
| System Monitoring | |||
| Issue Fixing | |||
| Maintenance & Support | Regular Updates | ||
| User Support |
62
Milestone Schedule:
| Milestone No. | Milestone Name | Start Date | End Date | Duration (Days) |
| M1 | Project Initiation | 2024-05-01 | 2024-05-15 | 15 |
| M2 | Project Definition and Planning | 2024-05-01 | 2024-05-05 | 5 |
| M3 | Requirement Collection and Analysis | 2024-05-06 | 2024-05-15 | 10 |
| M4 | System Design | 2024-05-16 | 2024-06-15 | 30 |
| M5 | System Development | 2024-06-16 | 2024-09-15 | 90 |
| M6 | Frontend Development | 2024-06-16 | 2024-08-15 | 60 |
| M7 | Backend Development | 2024-06-16 | 2024-08-31 | 76 |
| M8 | System Integration | 2024-09-01 | 2024-09-15 | 15 |
| M9 | Testing and Validation | 2024-09-16 | 2024-10-15 | 30 |
| M10 | Deployment and Release | 2024-10-16 | 2024-10-31 | 15 |
| M11 | Maintenance and Support | 2024-11-01 | 2025-04-30 | 180 |
| M12 | System Monitoring | 2024-11-01 | 2025-04-30 | 180 |
| M13 | Issue Resolution | 2024-11-01 | 2025-04-30 | 180 |
| M14 | Regular Updates | 2024-11-01 | 2025-04-30 | 180 |
| M15 | User Support | 2024-11-01 | 2025-04-30 | 180 |
Progress Schedule:
| Phase | Time Period | Key Tasks and Milestones |
| Project Initiation | Week 1-2 | - Project kickoff meeting - Define project team and responsibilities - Develop project plan and schedule |
| Requirement Analysis | Week 3-4 | - Collect and confirm requirements - Write functional specifications - Preliminary design of customer experience and communication module |
| System Design | Week 5-8 | - System architecture design - Database design - User interface design |
| - Functional module design | ||
| System Development | Week 9-30 | - Development and unit testing of functional modules - Home page (Week 9-11) - Customer experience and communication (Week 12-18) - Portfolio management and reporting (Week 19-28) - Business intelligence and compliance (Week 29-32) - Other modules like calendar, documents, emails, etc. (developed in parallel) |
| System Integration and Testing | Week 31-38 | - System integration testing - Functional testing and user acceptance testing (UAT) - Fix issues and retest |
| Deployment and Training | Week 39-42 | - Deploy system to production environment - User training and preparation of training materials - Final user training session |
| Project Acceptance and Support | Week 43-44 | - Final system acceptance - Provide ongoing technical support and maintenance plan |
| Risk Management | Throughout the project | - Weekly progress reports - Milestone assessments - Requirement change management process - Technical assessments and feasibility studies |
63
| 5. | Quality Assurance Measures |
| 5.1 | Quality Control Process |
Requirement Analysis Phase:
| ● | Requirement Review: Discuss requirements with customers and the project team to ensure all functional requirements are clear and achievable. |
| ● | Requirement Documentation Review: Write detailed requirement documents and organize review meetings to ensure document accuracy and completeness. |
Design Phase:
| ● | Design Review: Hold design review meetings in the early stages to ensure the design plan meets requirements and is feasible for implementation. |
| ● | Prototype Testing: Develop system prototypes and conduct user experience testing, collecting feedback for adjustments. |
Development Phase:
| ● | Code Review: Implement a code review system where each module’s code must undergo strict checks by team members before submission. |
| ● | Unit Testing: Developers must write unit tests for their respective modules to ensure functional correctness. |
Testing Phase:
| ● | Functional Testing: The testing team writes test cases based on requirement documents and verifies each functional module. |
| ● | Integration Testing: Ensures that modules work together after integration, identifying and resolving interface issues between modules. |
| ● | Performance Testing: Simulates real usage scenarios to perform system load testing and performance optimization, ensuring stable operation under high loads. |
Delivery Phase:
| ● | User Acceptance Testing (UAT): Invites customers for acceptance testing to ensure system functions meet customer requirements. |
| ● | Defect Fixing: Responds quickly to and fixes defects found during UAT, conducting re-acceptance confirmation. |
| ● | Documentation Delivery: Provides detailed system usage documents, maintenance documents, and training materials to ensure customers can smoothly use and maintain the system. |
Operation Support Phase:
| ● | Continuous Monitoring: Provides continuous monitoring services after system go-live to promptly identify and resolve operational issues. |
| ● | User Training: Organizes customer training to ensure users can proficiently use system functions. |
64
| ● | Technical Support: Provides long-term technical support services to quickly respond to issues encountered during use. |
Quality Control Roles and Responsibilities:
| ● | Project Manager: Supervises and manages the overall quality control process to ensure the project progresses as planned. |
| ● | Quality Assurance Manager: Develops the quality control plan, organizes reviews and testing activities at each stage. |
| ● | Development Team: Responsible for code development and unit testing, ensuring code quality and module functionality correctness. |
| ● | Testing Team: Writes test cases and performs functional, integration, and performance testing to ensure overall system quality. |
| ● | Customer Representatives: Participate in requirement reviews and UAT testing to ensure system functions meet business needs. |
Quality Control Tools and Methods:
| ● | Version Control System (e.g., Git): For code version management and code reviews. |
| ● | Project Management Tools (e.g., Jira): For task assignment, progress tracking, and issue management. |
| ● | Test Management Tools (e.g., TestRail): For test case management and test result recording. | |
| ● | Continuous Integration Tools (e.g., Jenkins): For automated building, testing, and deployment, improving development efficiency and quality. |
| 5.2 | Testing Strategy |
Functional Testing:
| ● | Objective: Verify whether each functional module works as expected. |
| ● | Method: Design test cases based on the functional specification document (SRS), covering all functional modules. Use a combination of manual testing and automated testing to ensure comprehensive testing. |
| ● | Tools: Selenium (for API testing). |
Performance Testing:
| ● | Objective: Assess the system’s response time and stability under different loads. |
| ● | Method: Perform load testing, stress testing, and capacity testing, simulating actual usage scenarios to evaluate system performance. |
65
| ● | Tools: Apache JMeter. |
Security Testing:
| ● | Objective: Ensure system security, preventing data leakage and unauthorized access. |
| ● | Method: Perform vulnerability scanning, penetration testing, and code reviews to identify and fix security vulnerabilities. |
| ● | Tools: OWASP ZAP. |
User Experience Testing:
| ● | Objective: Ensure the system interface is user-friendly and operations are smooth. |
| ● | Method: Collect user feedback through user surveys, usability testing, and A/B testing, optimizing system interface and interaction design. |
| ● | Tools: UsabilityHub. |
| 5.3 | Delivery Acceptance Criteria |
Delivery Standards:
| ● | System Function Acceptance: |
| o | Home Page: Acceptance criteria include page load speed, completeness of navigation bar functions, and response speed. |
| o | Customer Experience and Communication: Includes the completeness and accuracy of customer information management and communication records. |
| o | Portfolio Management and Reporting: Ensures report generation accuracy, data update timeliness, and chart presentation aesthetics. |
| o | Business Intelligence and Compliance: Ensures the accuracy of data analysis, completeness of compliance functions, and timeliness of anomaly detection. |
| o | Partners and Integration: Verifies the accuracy of partner information management, stability of integration functions, and real-time data synchronization. |
| o | Calendar, Documents, Emails, Marketing Campaigns, Call Records, Meetings, Tasks, Notes: Acceptance criteria include smooth operation, data integrity, and security of the above functional modules. |
| o | Invoices, Contracts, Cases: Verifies the accuracy of generated invoices and contracts, completeness of case management, and ease of querying. |
66
| o | Potential Customers and Potential Customer Lists: Ensures the accuracy of customer information entry, effectiveness of query functions, and convenience of list management. |
| o | Projects and Project Templates: Ensures the comprehensiveness of project management functions, accuracy of template generation, and data security. |
| o | Events and Event Locations: Verifies the reasonableness of event arrangements, accuracy of location information, and management convenience. |
| o | Products, Product Categories, PDF Templates: Ensures the accuracy of product information, rationality of category management, and aesthetics of PDF template generation. |
| o | Reports, Knowledge Base, Knowledge Base Categories: Ensures the accuracy of report generation, completeness of knowledge base information, and rationality of category management. |
| o | Email Templates, Surveys: Verifies the aesthetics of email templates, comprehensiveness of survey functions, and accuracy of data collection. |
| ● | System Performance Acceptance: |
| o | Response Time: All pages should load within 3 seconds, and backend processing response time should be within 2 seconds. |
| o | System Stability: The system should maintain stable operation under high concurrent access, ensuring no data loss. |
| o | Data Security: All user data should be encrypted to ensure the security of data transmission and storage. |
| ● | User Experience Acceptance: |
| o | Interface Friendliness: The interface design should be simple, aesthetic, and the operation process should conform to user habits. |
| o | Operational Convenience: User operations should be simple, reducing unnecessary steps to enhance operational efficiency. |
Acceptance Process:
| ● | Internal Testing: |
| o | Unit Testing: Conduct detailed unit testing for each functional module to ensure the correctness of module functions. |
| o | Integration Testing: After passing unit testing, perform integration testing to ensure module collaboration and overall system stability. |
| ● | User Testing: |
| o | Internal User Testing: Conduct testing by company internal employees, collecting user feedback and making improvements. |
67
| o | External User Testing: Select some customers for trial use, collecting feedback for further optimization. |
| ● | Final Acceptance: |
| o | Acceptance Report: Submit a detailed acceptance report, including test results, user feedback, and improvement measures. |
| o | Customer Signature Confirmation: Obtain customer signature confirmation after ensuring system functions and performance meet requirements. |
| ● | Post-Maintenance: |
| o | Maintenance Support: Provide one year of free maintenance support, including system upgrades, fault troubleshooting, and technical support. |
| o | Training Support: Provide system usage training to ensure customers can proficiently operate the system. |
| 6. | Risk Management Plan |
| 6.1 | Technical Risks |
Application of New Technologies: The use of new technologies or tools in the system may lead to unforeseen problems.
Technical Integration: Technical integration between modules may encounter compatibility issues.
Mitigation Strategies: Conduct technical research and small-scale trials in advance to ensure the feasibility of new technologies. Develop a technical integration plan to ensure seamless connection between modules.
| 6.2 | Time Risks |
Project Delays: Unexpected problems during development or testing may lead to project delays.
Insufficient Testing Time: Inadequate time allocation during the testing phase may affect testing quality.
Mitigation Strategies: Develop a detailed project plan and schedule with a buffer time. Timely identify and resolve issues during testing to ensure reasonable time allocation for the testing phase.
68
| 6.3 | Resource Risks |
Shortage of Human Resources: Insufficient testing team personnel or lack of necessary skills may hinder testing progress.
Insufficient Equipment and Tools: Insufficient hardware equipment and software tools for testing may affect testing execution.
Mitigation Strategies: Plan and allocate sufficient human resources in advance to ensure team members have necessary skills. Ensure the supply of testing equipment and tools, updating and maintaining them in a timely manner.
| 6.4 | Quality Risks |
Functional Defects: Functional defects in system modules may affect the normal use of the system.
Performance Issues: The system may be unstable under high load, affecting user experience.
Mitigation Strategies: Strictly implement functional and performance testing, promptly identifying and fixing defects. Continuously optimize to improve system performance and stability.
| 6.5 | Security Risks |
Data Leakage: Security vulnerabilities in the system may lead to user data leakage.
Unauthorized Access: Insufficient access control may allow unauthorized users to access the system.
Mitigation Strategies: Conduct comprehensive security testing, identifying and fixing security vulnerabilities. Strengthen access control to ensure user data security.
| 6.6 | User Experience Risks |
Unfriendly User Interface: Unreasonable user interface design may affect user experience.
Complex User Operations: Complex system operation processes may hinder user onboarding.
Mitigation Strategies: Collect user feedback through user experience testing and optimize user interface design. Simplify operation processes to enhance system usability.
69
| 6.7 | Risk Management |
Risk Monitoring:
| ● | Hold regular project meetings to assess the current risk status. |
| ● | Establish a risk monitoring mechanism to track and record risk changes in real-time. |
Risk Response:
| ● | Develop emergency plans to ensure rapid response when risks occur. |
| ● | Regularly evaluate the effectiveness of risk response measures and adjust as needed. |
Risk Communication:
| ● | Ensure effective communication within the team to promptly share risk information and response strategies. |
| ● | Maintain close contact with customers to keep them informed about project progress and risk status. |
| 7. | Project Deliverables |
| 7.1 | Final Deliverables List |
| No. | Deliverable Name | Description |
| 1 | System Requirement Specification (SRS) | Includes detailed descriptions of system functional requirements, non-functional requirements, business requirements, and system architecture. |
| 2 | System Design Document | Describes the system design plan in detail, including system architecture design, database design, module design, etc. |
| 3 | Source Code | All source code of the CRMAI system, including frontend and backend code repositories. |
| 4 | Test Cases | Test cases written based on functional requirements, covering functional testing, performance testing, security testing, and user experience testing. |
| 5 | Test Reports | Includes detailed results of all tests and identified issues, summarizing defects and improvement suggestions during the testing process. |
| 6 | User Manual | User guide provided to end users, detailing the usage methods and considerations of each functional module of the system. |
| 7 | Technical Manual | Technical documentation provided to developers and maintenance personnel, including detailed descriptions of system configuration, deployment, maintenance, and updates. |
| 8 | Training Materials | Training materials prepared for users and system administrators, including PPTs, video tutorials, and operation guides. |
| 9 | Deployment Document | Details the steps, environment configuration, and considerations for system deployment to ensure correct installation and operation of the CRMAI system. |
| 10 | Database Scripts | SQL script files for creating and initializing databases, including table structures, initial data, and stored procedures. |
| 11 | Installation Package | Installation package and installation guide for the system, used for installing and configuring the CRMAI system in the target environment. |
| 12 | Configuration Files | Configuration files required for system operation, including system parameter configuration, environment configuration, and security configuration. |
| 13 | Project Summary Report | Summary of the project implementation process, including project background, implementation process, encountered problems and solutions, project achievements, and future suggestions. |
| 14 | Source Code Version Control Records | Records the version history of the source code in the version control system, facilitating tracking and tracing code modifications. |
| 15 | System Demonstration Video | Recorded system functionality demonstration video, showcasing the main features and usage processes of the system. |
| 16 | Customer Acceptance Test Report | Detailed results of customer acceptance testing, including issues and feedback raised by customers and corresponding improvement measures. |
| 17 | Service Agreement | Technical support and maintenance service agreement for the system after go-live, clarifying the responsibilities and obligations of both parties. |
70
| 18 | Data Backup and Recovery Plan | Data backup and recovery plan for the system, ensuring data security and high availability of the system. |
| 19 | Security Audit Report | Detailed report of security testing and audit, including identified security issues and improvement suggestions. |
| 20 | User Feedback Records | Collected and organized user feedback, recording users’ opinions and suggestions on the system. |
| 7.2 | Operations and Maintenance Support Plan Monitoring and Alerts: |
| ● | System Monitoring: |
| o | Real-time monitoring of key indicators such as servers, databases, and network traffic. |
| o | Setting up monitoring strategies using tools like Nagios and Zabbix to ensure timely detection of issues. |
| ● | Alert Mechanism: |
| o | Setting up alert rules to send timely notifications (such as SMS and emails) when system indicators exceed predefined thresholds. |
| o | Ensuring the timeliness and accuracy of alert notifications. |
Maintenance and Updates:
| ● | Regular Maintenance: |
| o | Regularly checking system logs to identify and resolve potential issues. |
| o | Regularly updating system components to ensure the system operates on the latest versions. |
| ● | System Updates: |
| o | Regularly releasing system updates as needed, including functionality enhancements and vulnerability fixes. |
| o | Thorough testing before updates to ensure they do not affect system stability. |
Data Backup and Recovery:
| ● | Data Backup: |
| o | Developing data backup strategies and regularly backing up databases and important files. |
| o | Backup frequency: daily full backups and hourly incremental backups. |
71
| ● | Data Recovery: |
| o | Developing data recovery plans to ensure quick recovery in case of data loss or damage. |
| o | Regularly conducting data recovery drills to ensure the feasibility of recovery plans. |
Fault Handling:
| ● | Fault Response: |
| o | Establishing a fault response team with clear responsibilities and contact information for each member. |
| o | Developing fault response processes to ensure quick response and handling when faults occur. |
| ● | Fault Troubleshooting: |
| o | Using troubleshooting tools to quickly locate and resolve issues. |
| o | Regularly summarizing fault handling experiences to optimize fault handling processes. |
Performance Optimization:
| ● | Performance Monitoring: |
| o | Regularly conducting performance tests to evaluate system performance under different loads. |
| o | Continuously monitoring system performance using tools like APM (Application Performance Management). |
| ● | Performance Optimization: |
| o | Optimizing system architecture and code based on monitoring results and test feedback. |
| o | Optimizing database queries and indexes to improve data processing efficiency. |
72
Customer Support:
| ● | Customer Training: |
| o | Providing system operation training for customers, including online and on-site training. |
| o | Providing training materials and operation manuals to help customers get started quickly. | |
| ● | Technical Support: |
| o | Providing 24/7 technical support to ensure customers can get help at any time. |
| o | Establishing customer support hotlines and email support channels to respond to customer issues promptly. |
| ● | Customer Feedback: |
| o | Regularly collecting customer feedback to understand their needs and issues encountered during use. |
| o | Continuously improving and optimizing the system based on feedback to enhance customer satisfaction. |
Emergency Plans:
| ● | Disaster Recovery: |
| o | Developing disaster recovery plans to ensure quick system recovery in case of major faults. |
| o | Regularly conducting disaster recovery drills to ensure the feasibility and effectiveness of the plans. |
| ● | Business Continuity: |
| o | Developing business continuity plans to ensure business operations can continue during system faults. |
| o | Configuring backup systems and disaster recovery plans to enhance system availability. |
| 8. | Other Supporting Documents |
73